misc
签到
侧信道初探
根据提示用侧信道简单能量分析攻击 SPA 就可以从芯片的功耗曲线中可以读出十六进制的关键数据。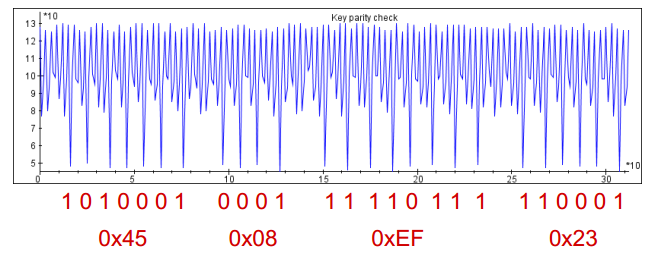
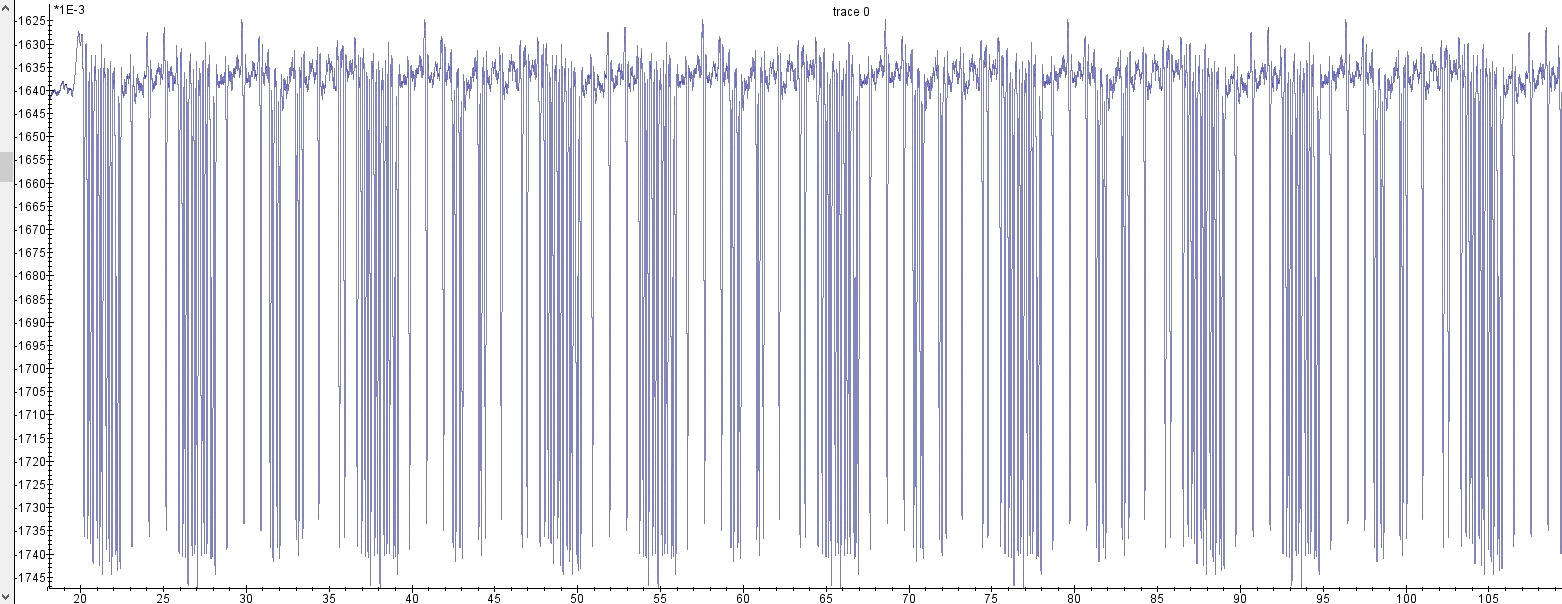
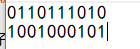
因为不知道哪个是0哪个是1 然后试了一下
SCTF{0110111010}
神奇的Modbus
modbus协议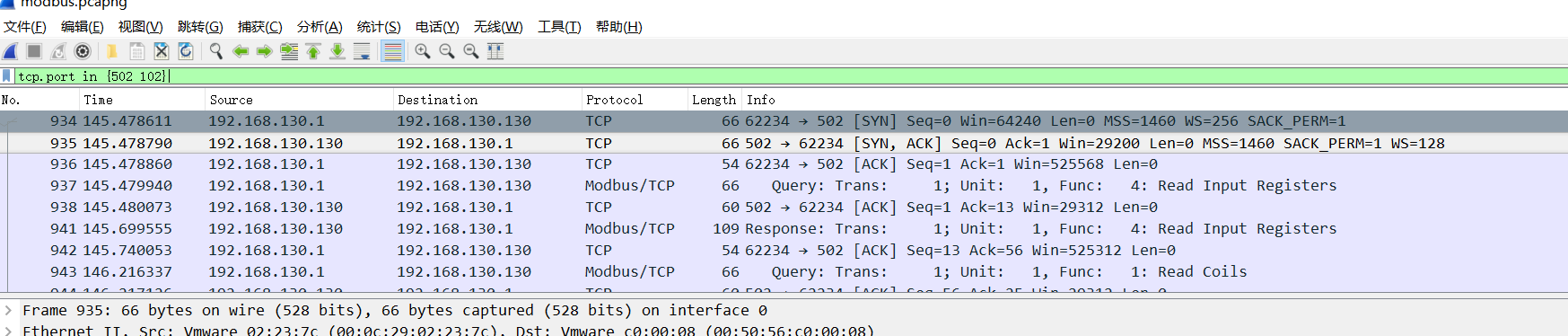
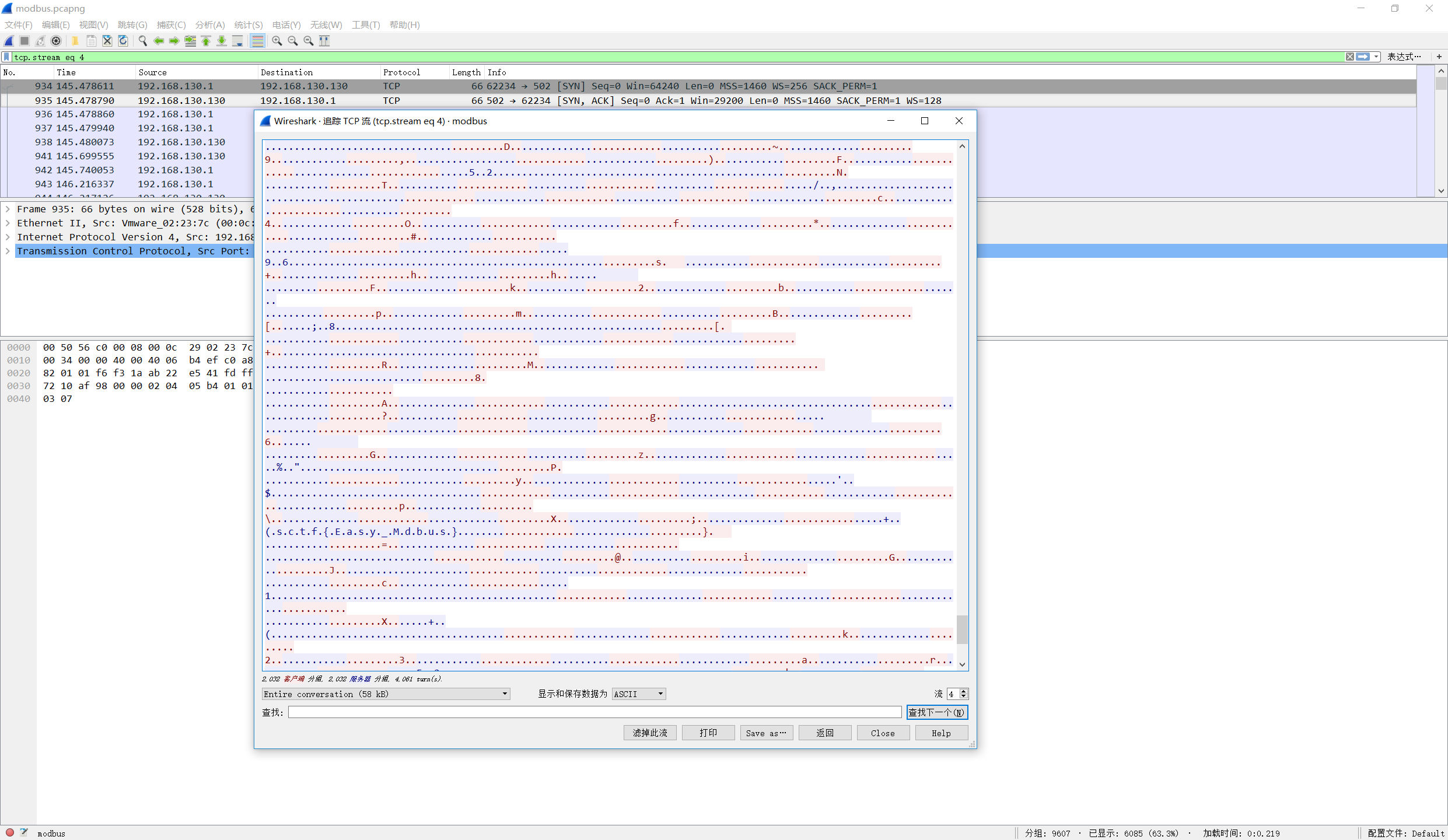
按照网上一道类似题的分析,找TCP/IP协议502,102端口
追踪TCP流
SCTF{Easy_Mdbus}
神秘的交易
百度找到看雪的一篇分析文章
logicdata拖进Logic里面,分析嗅探得到的波形图1
2
30x33 0x01 s1
0x33 0x02 s2
0x33 0x03 s3
读出s1, s2, s3

SCTF{403110}
肥宅快乐题
用爱奇艺可以拖flash 然后直接拖到最后看了几遍什么都没发现 然后往前翻 发现中间有个过程动画(大概57那里)与那个boss对话中有段base64 解码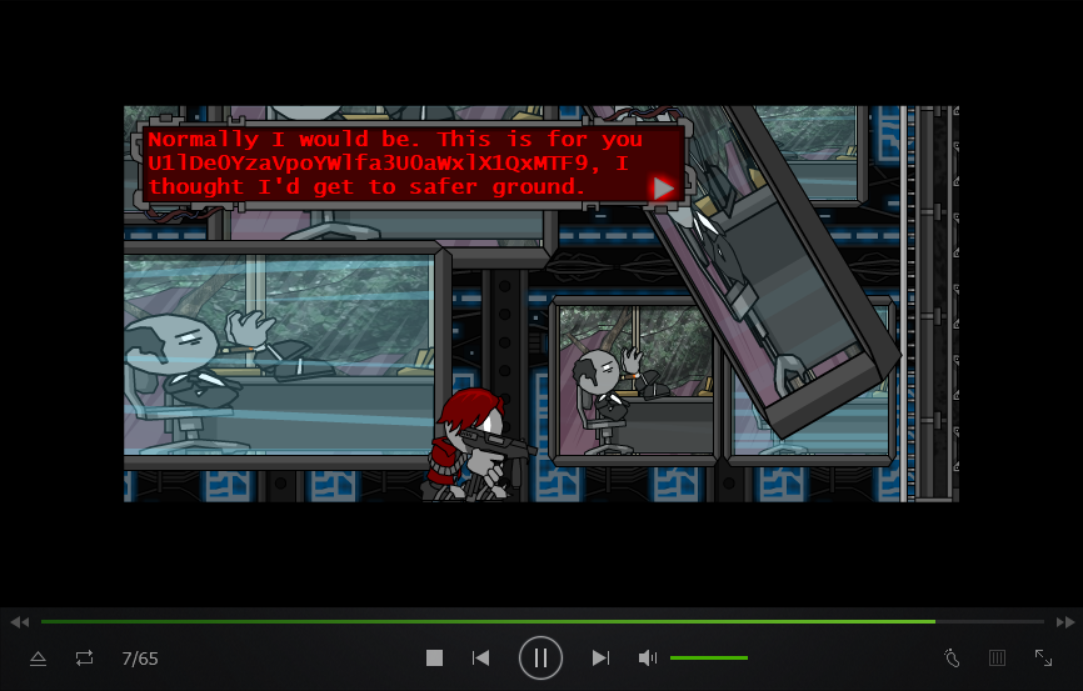
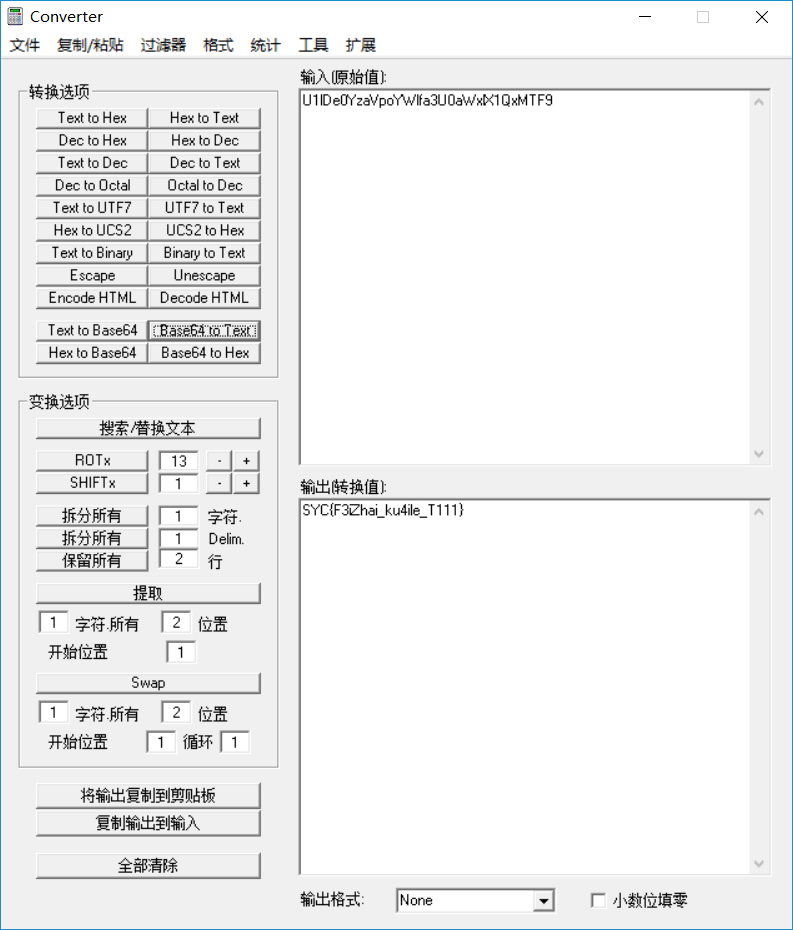
base64解码
SYC{F3iZhai_ku4ile_T111}
CRYPTO
it may contain ‘flag
给出了n, e, c 求m
首先尝试了一下分解n,结果太大分解不出来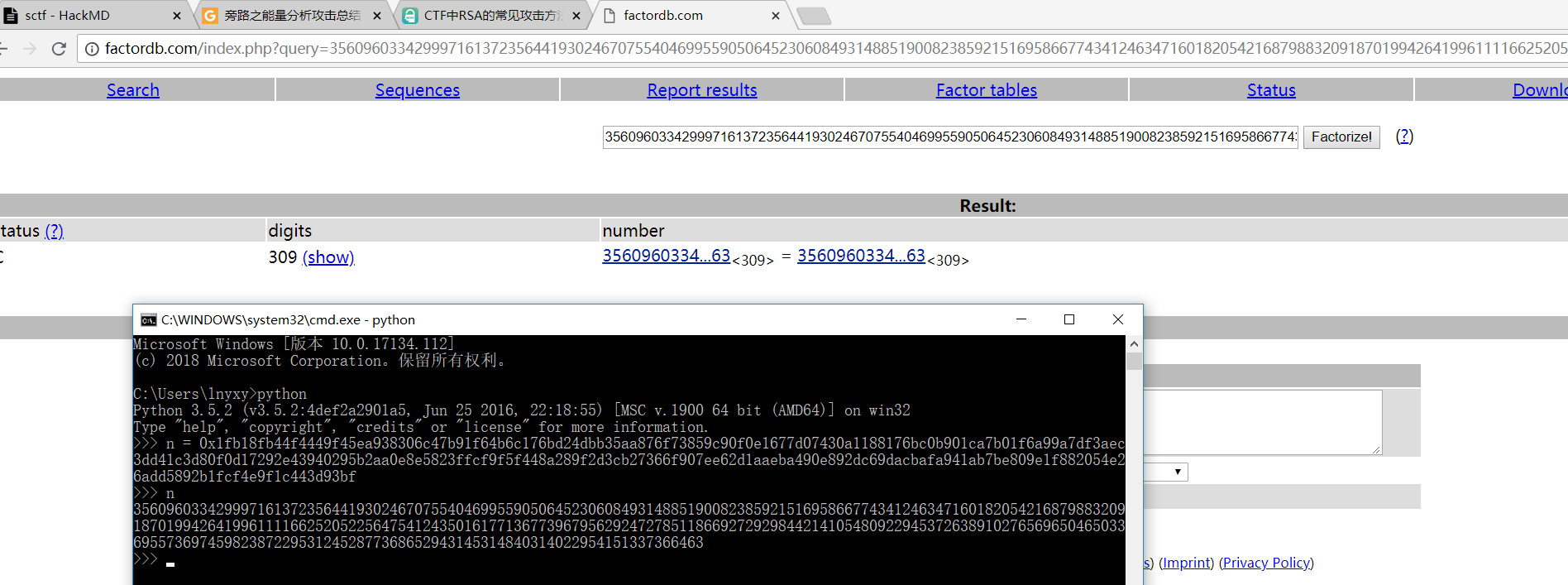
看了一下RSA相关文章 用低解密指数攻击
特征:e看起来非常大
github 上有RSAwienerHacker 直接下下来跑一下1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62import ContinuedFractions, Arithmetic, RSAvulnerableKeyGenerator
def hack_RSA(e,n):
'''
Finds d knowing (e,n)
applying the Wiener continued fraction attack
'''
frac = ContinuedFractions.rational_to_contfrac(e, n)
convergents = ContinuedFractions.convergents_from_contfrac(frac)
for (k,d) in convergents:
#check if d is actually the key
if k!=0 and (e*d-1)%k == 0:
phi = (e*d-1)//k
s = n - phi + 1
# check if the equation x^2 - s*x + n = 0
# has integer roots
discr = s*s - 4*n
if(discr>=0):
t = Arithmetic.is_perfect_square(discr)
if t!=-1 and (s+t)%2==0:
print("Hacked!")
return d
# TEST functions
def test_hack_RSA():
print("Testing Wiener Attack")
times = 5
while(times>0):
e,n,d = RSAvulnerableKeyGenerator.generateKeys(1024)
print("(e,n) is (", e, ", ", n, ")")
print("d = ", d)
hacked_d = hack_RSA(e, n)
if d == hacked_d:
print("Hack WORKED!")
else:
print("Hack FAILED")
print("d = ", d, ", hacked_d = ", hacked_d)
print("-------------------------")
times -= 1
if __name__ == "__main__":
#test_is_perfect_square()
#print("-------------------------")
test_hack_RSA()
n = 356096033429997161372356441930246707554046995590506452306084931488519008238592151695866774341246347160182054216879883209187019942641996111166252052256475412435016177136773967956292472785118669272929844214105480922945372638910276569650465033695573697459823872295312452877368652943145314840314022954151337366463
e = 160222447153262895889250928158012827757109871196102040037421857250766491575699886894325697077956068896677359953037375582060511979328323570880578946073240834317364119936983046746942944368567355131867682895196198904859001202051459879133425754080440276218324680838480108302184726980362910704693149535052743526713
c = 147196512678165362278479859274730376684762864061315836792770099383278172248558388764516679102190414689292831454764081139184450400390951627813402530351267384900672105846731222258018693047922255488857215383862135296386187138430843389538652580147662346075434257219061071710799682137566072656776621262987516040147
d = hack_RSA(e, n)
print(d)
m = pow(c, d, n)
print(m)
print('%#x'%m)
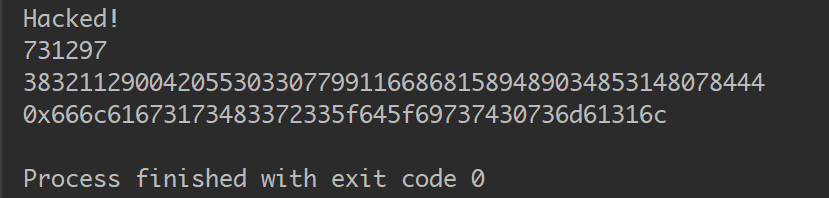
提交十进制十六进制都不对,转一下十六进制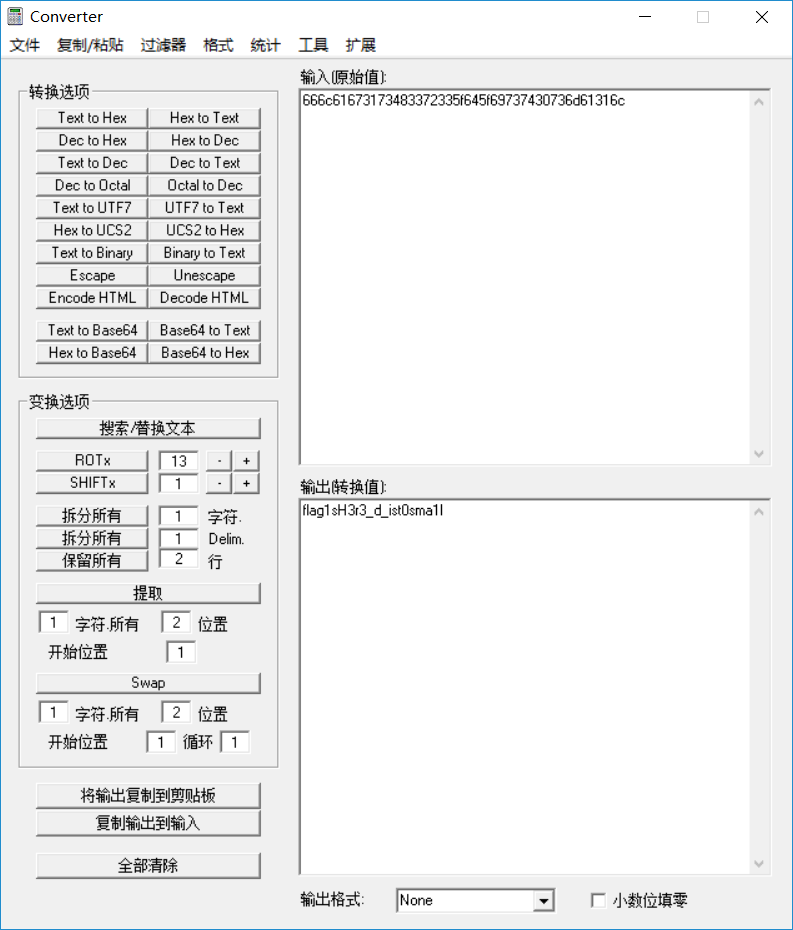
get flag
贴个官方WP